In a networked digital milieu, how do you study cultural practices that you’re not supposed to know about? How do you examine the digital objects related to those practices, when – from the perspective of formal copyright economies – they shouldn’t exist? How do you map the erratic, temporary circulatory networks that these objects describe? How do you discern the subject positions within such networks when the people who occupy them as producers and consumers wish to remain pseudonymous or anonymous? And why bother at all?
This paper presents the initial findings from a study of the production, transmission and consumption of unauthorized comic book scans (“scans” for short). In the process, it demonstrates a research method with practical, ethical and theoretical implications for the emerging subdiscipline of network archaeology. It also presents a reminder that we can and should think about digital popular culture in relation to fields other than literature or music. And it argues that the practices of comic book scanners – frequently described as “pirates” by online journalists, if rarely by the scanners themselves – are worth studying not just because of their specificity, but in part because they offer insights into the functioning of digital cultures of circulation in general. If the circulatory practices of comic book scanners (“scanners”) were once obscure and arcane, something very similar to them has now become commonplace, and perhaps even characteristic of contemporary digital culture.
Information Curation as Digital Piracy
In December 2010, after the annual Technorati “State of the Blogosphere” report, digital media pundit Brian Solis proclaimed “2011 is the year of information curation and the dawn of the curator”:
In social media, a curator is the keeper of the interest graphs that are important to them. By discovering, organizing, and sharing relevant and interesting content from around the Web through their social streams of choice, curators invest in the integrity of their network as well as their relationships. Information becomes currency and the ability to recognize something of interest as well as package it in a compelling, consumable and also sharable format is an art. Curators earn greater social capital for their role in qualifying, filtering, and refining the content introduced to the streams that connect their interest graphs.1 The implicit argument is that this protocol has become necessary because unregulated information curation is the gentrified form of what is often referred to as digital piracy (a revelation that will surprise no one familiar with the postcolonial critique of museums as institutions in the service of cultural imperialism, whose “discoveries” are often tantamount to looting).
Certainly the rhetoric of the Times article describes “naughty curation” in terms that position its practitioners as outlaws. The Internet is a “digital Wild West.” “Traditional media organizations watched as others kidnapped their work.” Digital curation is “analogous to pornography” because “you know it when you see it.” In the freebooting digital environment, “what’s yours may not be yours anymore if others find a better way to package it.” Even the virtuous version of digital creation is painted in piratical terms, as a search for a buried treasure of “little gems” to “unearth.”2
On YouTube, Facebook, Pinterest, Tumblr and the other social networks, we continually encounter, recontextualize and recirculate digital copies of cultural objects, with little regard for their provenance or copyright. Occasionally, the objects we circulate are also things that we create. Inflammatory rhetoric aside, what’s significant is the similarity in cultural practices between the activities of information curation and comic scanning. One major difference is contextual: the social networks domesticate circulation by corralling users into “stacks”3 where their activities can be algorithmically monitored and policed by technologies like YouTube’s Content ID.4 If we wish to better understand the other similarities and differences between sanctioned and unsanctioned networks of digital circulation, as well as the complex interactions between them, it is worth taking the time and effort to study informal economies like comic book scanning. This is not an apology for the practices of scanners. It is an observation that these practices are a significant but fragile part of our digital history, and that we are in the process of erasing them. Online, as elsewhere, we need historical and cultural context for who we are and what we do. The question of how to proceed with such research is another matter.
One Million Manga Pages and Method
In 2010, Lev Manovich’s Software Studies initiative released a draft paper by Jeremy Douglass, William Huber and Manovich, titled “Understanding Scanlation: How To Read One Million Fan-Translated Manga Pages.”5 If academics have thought at all about comic books and scanning practices, it’s probably in the context of this project, which deals with a similar set of objects to our own, but applies a different set of tools, and draws very different conclusions. The Understanding Scanlation project makes use of a custom software system running on a supercomputer at The National Department of Energy Research Center and the 287-megapixel Highly Interactive Parallelized Display Space (HIPerSpace), with custom software for interactive exploration of large image sets developed by softwarestudies.com and the Calit2Gravity lab.
There’s much to admire about this project. The researchers remark that we need to develop a critical vocabulary capable of describing manga scanning (or “scanlation”) as a complex set of cultural practices. We need to know more about manga and comic scans as physical artifacts, and we need to know more about their modes of production, reception and circulation.6
In proximity to new high-end hardware, digital media researchers often experience a very specific form of intoxication. In his extended essay on operating systems titled In the Beginning … Was the Command Line, science fiction writer Neal Stephenson uses an analogy between consumer-grade and contractor-grade power drills to describe the difference between commercial operating systems and GNU/Linux. For Stephenson, GNU/Linux is like the Milwaukee Electric Tool Corporation’s Hole Hawg, an ugly but astonishingly powerful device. He relates several workplace safety horror stories about himself and his coworkers being flung around like the proverbial frog in a blender by the drill’s mighty motor on those instances when its bit jammed. “[It’s] like the genie of the ancient fairy tales, who carries out his master’s instructions literally and precisely and with unlimited power, often with disastrous, unforeseen consequences,” he writes.7 Despite this caveat, the promise of the tool’s power has thoroughly interpellated him: he concludes that he now views consumer-grade hardware “with such contempt that I do not even consider them to be real drills – merely scaled-up toys designed to exploit the self-delusional tendencies of soft-handed homeowners who want to believe that they have purchased an actual tool.”8 This comparison implies that computing, even the word-processing of a science fiction writer, should be unthinkable without the use of GNU/Linux; the tool’s power becomes its own justification, regardless of its applicability to the task at hand.
To return to “Understanding Scanlation,” the problem is that the conclusions of the vast and expensive enterprise it describes are largely self-justifying. What they do, for the most part, is provide a rationale for using supercomputers to think about manga. By virtue of the exclusion of questions of materiality, production, circulation and consumption from consideration, what’s left to study is the amount of ink on the page. The verdict is simply a justification for the use of their chosen tools: “if we find a very large number of variations with very small differences between them (such as in this case of 1 million Manga pages), it is no longer possible to talk about ‘style’ of these works. Instead, it is better to use visualization and/or mathematical models to describe the space of possible and realized variations.”9 Manovich et al. use a 2-D matrix to display their dataset, with the y axis measuring graphic detail, and the x axis measuring contrast. As graphs go, it tells us very little about the relationship of the objects in the dataset to culture because of the specific variables that have been chosen for the graph. What’s compelling about this dataset is not its visual content, but the material, social and circulatory aspects that the authors mention then dismiss in the interests of providing a usage case for their hardware. Analysis of these factors could incorporate visualization and mathematical models, but would require much more of the “traditional digital humanities hand-tagging approach” that the researchers disparage10 (not to mention the question of how anything in digital humanities method can be considered “traditional” at this point).
Without access to specialized hardware and the enormous budgets that it entails, it’s still possible to conduct network-archaeological research that takes the production, reception, and circulation of large numbers of digital objects into account. Moreover, the distinction between the practices of information curation and comic book scanning and their respective articulations to culture lies in studying precisely how and why scanners make, circulate, and use their scans.
From Subcultures to Formats and Networks
The historical underpinnings for theory behind our approach to the study of comic book scanning are in the cultural studies of another sort of social grouping and its treasured objects – namely, music fans and the artifacts of popular music. The vast literature around the study of popular music communities and forms has gradually shifted from an emphasis on subculture in the 1970s to networks of articulation and circulation in the 21st century.11 The combination of this body of work with insights from platform studies12 and software studies13 (subdisciplines of media theory) and a general theory of discourse, assemblages and networks14 provides a sophisticated, flexible context in which to consider both qualitative and quantitative data about scanners, scanning and scans.
The notion of subculture, as famously developed by Dick Hebdige and the other members of the Birmingham Centre for Contemporary Cultural Studies in the 1970s around various musical demimondes,15 might initially seem very attractive as a starting point for discussing scanners. However, as Andy Bennett reasons, “the term ‘subculture’ is also deeply problematic in that it imposes rigid lines of division over forms of sociation which may, in effect, be rather more fleeting, and in many cases arbitrary, than the concept of subculture, with its connotations of coherency and solidarity, allows for.”16 If this was true of music culture in the 70s and 80s, it goes double for scanners, who rarely if ever meet each other face-to-face, change aliases regularly, and change allegiances between release groups. David Hesmondhalgh rejects Bennett’s alternative to subculture – a form of neo-tribalism – on the grounds that where a mix of qualitative and quantitative data would be necessary to support the concept, Bennett relies only on the qualitative, and his theoretical framework remains unsupported.17 Hesmondhalgh then works through and ultimately abandons first Barry Shank’s18 and Will Straw’s respective mobilizations of the concept of “scene”19, on the grounds that even though the term is useful precisely because it doesn’t assume or require physical locality20 (which would be a prerequisite for its use to describe comic scanning), it “has been used for too long in too many different and imprecise ways for those involved in popular music studies to be sure that it can register the ambivalences that Straw hopes it will.”21 What Hesmondhalgh offers in its place is not a new master concept, but “an eclectic array of theoretical tools to investigate the difficult questions towards which the terms subcultures, scenes and tribes direct our attention,” in which the concepts of genre and articulation play major roles.22
Hesmondhalgh’s approach to genre doesn’t rely on categorical lists of texts. Instead, he adopts the influential approach from Steve Neale’s book on genre, which describes genres as “systems of orientations, expectations and conventions”23 that connect audiences to both texts and the industries that produce them, effectively describing a political economy of circulation. This is helpful, but requires some modification because scanners work primarily with changes in medium (producing digital copies of print comic books) and format (image sizes and resolutions, data storage standards, metadata) rather than genre (though some scanner activities, such as compiling multiple book-length scans for inclusion in a single file or torrent, can proceed along genre lines). In both print and digital textuality, the relationship between medium, format and genre is a continuum, as both Charles Bernstein24 and Lisa Gitelman25 have described. Gitelman’s formulation is particularly helpful, because it draws a parallel between the relationship of medium, format and genre in print and the lower levels of the analysis model that platform studies uses to describe digital systems (platform, game code, game form, interface, reception and operation, all permeated by social context).26 Jonathan’s Sterne’s description of digital formats (the MP3, in his particular case) as “crystallized set[s] of social and material relations” hearkens back to what’s most useful about Neale’s concept of genre, because formats describe objects that “work for” and are “worked on” in turn “by a host of people, ideologies, technologies and other social and material elements.”27 Paying attention to format in these ways when thinking about scan and scanning will provide both a respect for the material objects themselves, and an awareness of their embeddedness in larger networks of production, circulation and consumption.
To think about format, in other words, is to think about not just the materiality of objects, but about the orientation of those objects, as well as their users and makers, toward culture. Hesmondhalgh also maintains that we need Stuart Hall’s theory of articulation28 in our conceptual toolbox.29 Articulation is a powerful and versatile concept, describing the “form of connection” that can unite two different elements, under specific conditions and for uncertain durations. It is a way of describing the relations of subjects and objects to social formations via discourse that is specifically ideological, accounting for the ways in which “an ideology discovers its subject” and in turn enables the subject to make sense of their specific historical situation without necessarily reducing that sense-making process to questions of class or social position.30 However, as with the shift from a focus on genre to a focus on format, we need to retrofit the concept of articulation for use in networked culture. Hall provides a theory of linkage, which is an essential component of any network, but it is not iself a theory of networks, which are assemblages that consist of linkages.31 Hesmondhalgh and Georgina Born’s elaboration of this notion into a network of “multiple articulations” comes closer, as does the contention that cultural forms “can variably both construct new identities and reflect existing ones.”32 We need to think in terms of an ever-changing network of connecting, disconnecting and reconnecting articulations that continually produces transfigurations in its particular objects, subjects and discourses.
Straw’s more recent work, following that of Dilip Gaonkar and Elizabeth Povinelli on the circulatory turn,33 animates the network of articulations, inviting us to inquire about “how the movement of cultural forms presumes and creates the matrices of interconnection which produce social texture.”34 In our specific context, the circulation of scans both requires and creates the social network of scanners and readers through which they move. Circulation theory also has the virtue of providing an account of how the circulation of cultural forms like scans results in their “dynamic transfiguration”35 – not only does print become digital, but specific file formats and compression standards are chosen, image sizes are agreed upon, ranges for colour correction develop. As these cultural forms circulate, their “edges” not only define the contours of the network, they also act as the interfaces through which we encounter such networks36 – again, in our case, specific software applications appear which allow for new ways to interact with the results of the series of transfigurations that scanned comics undergo. Our task becomes the description of “a set of circulatory fields populated by myriad forms, sometimes hierarchically arranged and laminated but mostly undulating as an ensemble, as a melange, going about their daily reproductive labour of mediating psychosocial praxis.”37 From the relative beginnings of comic enthusiasts and a mixture of print and digital comics, circulatory fields form to create and circulate digital comic scans, bringing new kinds of objects, subject positions and discourses of legitimation and guilt into being as they do so. New practices develop, which transfigure the subjects and objects and discourses within them in turn.
Broken Metaphors in the Rear-View Mirror
As Marshall McLuhan famously observed, “We look at the present through a rear-view mirror. We march backwards into the future.”38 One of the results of this specular arrangement is that we always begin the description of emergent medial phenomena with inappropriate metaphors, drawn from the realm of the known. McLuhan’s pet example was the “horseless carriage” as an epithet for the automobile. “But the horseless carriage did not do the work of the horse; it abolished the horse and did what the horse could never do. Horses are fine. So are books.”39 The comic scan is our horseless carriage. So what does it mean to refer to scanners as “pirates” in an unqualified manner?
In the 21st century, there are once again actual, non-metaphorical pirates on the oceans of the world.40 Though they’re frequently described as such,41 if comic book scanners are pirates, they’re pretty miserable specimens, as comic scanners invest significant amounts of time and money over the years that they are active42 into an activity that rarely returns anything43 but meager scraps of subcultural capital. (During the peak years of digital comic scanning, actual Somali pirates were netting about $120 million.44 ) As Adrian Johns has argued at length in his magisterial study Piracy: The Intellectual Property Wars from Gutenberg to Gates, the metaphor of piracy for intellectual purloining is integral to the production of modernity itself, so we’re stuck with it, at least until digital piracy precipitates a crisis that transforms that very order into something else.45 While we’re waiting, it would be wise to remember Johns’ admonition that “A culture of piracy was one that could never be distinguished into two neat camps of the honorable and the dishonorable in the way that antagonists often professed to believe. Everyone involved was, to some extent, compromised.”46 It is just such an environment of mutual compromise that creates the condemnatory discourse that envelops both comic scanning and information curation.
The metaphor of digital copying and peer-to-peer circulation as “archiving” also requires some scrutiny, because of its newfound popularity in a networked digital context. In an early article on LOCKSS (Lots of Copies Keep Stuff Safe), a digital tool that allows libraries to ensure ongoing access to digital journals, Vicky Reich and David S. H. Rosenthal distinguish between the way that an archive functions and the way that networked digital preservation tools function. Where archives drastically limit access to maximize the protection of materials that are difficult to replicate, digital systems combine the process of making their materials available with the action of preservation. The result is that what is preserved is not original, but a multitude of copies, often materially different from each other even if their ostensible “content” is the same.47 As a result, scholars including Julia Martin and David Coleman reason that “the very notion of a permanent or fixed archive may have to give way to an ecological preservation system that (paradoxically perhaps) is in a state of constant change.”48 If scanners and readers of digital comics are archiving anything, it is only in this second, ambiguous sense of the term.
Our larger argument is that the study of the circulation of unauthorized comic book scans is an exemplary case for the development of the theory and methods of network archaeology. When we study texts in a networked digital milieu, scans included, what we are actually facing is a set of circulatory practices that define particular network economies. Again, though he does not discuss comic book scanning directly, Johns is helpful here: “the history of piracy is a matter of not just precepts but practices – artisanal crafts, policing strategies, ways of reading, and the like.”49 In the case of the economy that surrounds scans, we need to consider the practices of the various communities of comic book writers, artists, colourists, publishers, retailers, scanners, editors, uploaders, readers, commentators, policing and regulatory bodies, scholars studying the subject, and so on. Further, these practices also have particular geographies, spatialities and temporalities: “piracy was a property not of objects alone, but of objects in space.”50 Like the circulation theorists, Johns notes that the process of circulation also transfigures the circulating objects themselves,51 meaning that we are never dealing with a set of coherent things, but with a dynamic network of files that bear something like a family resemblance to each other.52 In sum, the project of studying the circulatory networks of comic scans and scanners raises a thicket of practical questions for potential network archaeologists.
Challenges
An informal economy such as the one that has developed from the circulation of unauthorized comic book scans magnifies the sorts of problems that anyone researching more commonplace aspects of Internet culture will encounter.
First, all files have multiple, relative origins. The oldest consistent sources for scanned comics on the Internet are encoded binaries on the Usenet newsgroups alt.binaries.pictures.comics and alt.binaries.pictures.comics.dcp. However, scanned comics have also always appeared on Internet Relay Chat (IRC) channels, peer-to-peer networks like DirectConnect and BitTorrent, and various file locker sites (RapidShare, MediaFire, MegaUpload, FilesTube, etc.) with frequent pointers from websites and Twitter accounts. Different uploaders sometimes change the names of files to suit their own storage systems. Sometimes the same books have been scanned multiple times by different people, resulting in parallel editions. Scans are also re-edited to remove errors, correct colours, remove ads and insert additional material, such as alternate covers.
When you can find these files, they don’t stay in the same place for very long. Though Usenet was once the dominant component of popular traffic on the Internet, hacker history has it that Usenet has been in decline since the “eternal September” of 1993, when “AOL users became able to post to Usenet, nearly overwhelming the old-timers’ capacity to acculturate them; to those who nostalgically recall the period before, this triggered an inexorable decline in the quality of discussions on newsgroups.”53 Google, the largest archiver of Usenet posts, doesn’t archive the alt.binaries.comics and comics.dcp newsgroups (or at least doesn’t make them available to the public if they do). Most Internet Service Providers no longer make Usenet part of their standard subscription package, but there are still a few specialized Usenet providers like Giganews and Unison available for those interested in the service. The former stores binary files for a maximum of 1640 days (four and a half years),54 but that is the upper limit; the latter provides only 300 days of binary storage.55 Further, the comic files that Torrent indices describe are totally evanescent, because they are always located on the hard drives of the various seeders connected to the swarm.
To complicate matters further, the climate of the Web is changing in ways that make it far less easy to share data, whether the intent is legitimate or illegitimate. Tim O’Reilly launched his inaugural Web 2.0 conference in 2004 to explore the technologies that turned the Web from a read-only environment into one that was writable and more amenable to the syndication of information, but, as his business partner Bryce Roberts points out, he hypothesized that it would eventually end in a series of data monopolies.56 On April 4, 2012, the Web 2.0 conference went on indefinite hiatus,57 suggesting that O’Reilly for one believes that the time of data monopolies is upon us. Supporting evidence is not hard to find; social software services like Twitter and Facebook are more and more invested in turning their networks into digital pitcher plants. What the atmosphere of increased policing and decreased flexibility means is that infringing activities move elsewhere, to the sorts of spaces that Peter Biddle et. al. presciently dubbed “the darknet.”58 As the comic scans and other material housed on peer-to-peer services like DirectConnect, or on members-only sites like LUElinks,59 is largely invisible, this causes real difficulties for scholars interested in studying it.
The changing legal climate of the Web is also affecting the persistence of data about the location of files, making it more difficult to find them, or even describe them. In late 2010, Kent Walker, general Counsel for Google, announced that the search engine would be implementing a number of changes to make potentially infringing material less visible in its searches, including acting on reliable takedown requests within 24 hours, preventing terms “closely associated with piracy” from appearing in the Google AutoComplete dropdown menu, and making changes to its AdSense system to more thoroughly exclude those seeking to profit from the advertising of potentially infringing materials.60 When Google excludes or downgrades domain names like “The Pirate Bay” “BitTorrent” and “MediaFire” in its search results, the number of searches for those terms drops significantly as a result.61 Its is always possible to use other, less discerning search engines, of course, but Google’s hegemony over search makes that choice less likely with each passing moment.62
When it is still possible to find information about where files are, or were, it is often difficult or impossible to come up with reliable statistics about their actual use. While torrent descriptor files have the virtue of providing complete indices of torrent contents, they aren’t reliable indicators of total numbers of downloads that have occurred, or of the origins of the torrent.
Until now, we haven’t mentioned the problem of actually retrieving files, because it isn’t relevant to our own research. As Friedrich Kittler has argued, media storage may be the precondition for distribution and processing,63 but, as per our discussion of why archiving is a poor metaphor for peer-to-peer circulation, it’s crucial to recognize that distributed storage doesn’t necessarily allow retrieval. After the Pirate Bay trial64 and the MegaUpload raid,65 locker sites like MediaFire began adding the “noindex” meta tag to all new and extant files in early 2012, in order to make them non-searchable.66 Even the descriptor files for torrents that we have been collecting for our own research started to disappear from tracker sites around this time. Digital networks are profoundly space-biased, in Harold Innis’ sense,67 meaning that while they excel at propagating information quickly and promiscuously over vast distances with great speed, constructing and destablizing empires by turn, they’re next to useless for long-term preservation, at least in the sense that we think of when we’re considering conventional archival practice. As Alan Liu notes elsewhere in this issue, the past is part of a network assemblage too, but we need to treat past and present networks differently because they have different topologies. The takeaway for network archaeology here is partly methodological: capture everything immediately, then database it, because, by the time their research is ready for publication, scholars will face the very real possibility that they are the only ones with a copy of the data their research describes.
The changing materiality of comics themselves means that the practices that structure the entire economy of comic book “scanning” (unauthorized or otherwise) are currently in transition. Much if not all of the production cycle of many new comics, from scripting to drawing board to colouring, lettering, processing, marketing, sales, delivery, and reception, is now digital. As the name suggests, comic scanning has traditionally involved people making digital copies of analog objects. This practice might continue unabated with people making scans of older titles, which are in no risk of being exhausted because of the aforementioned factors that make retrieval of any given comic book scan unreliable. But is there any evidence that unauthorized comic book circulation is changing to adapt to all-digital circulation?
An increasing number of the scanned comics in circulation are clearly not scans at all, but digital prepress versions that have been leaked or pilfered off of publishers’ servers during the production cycle. In February 2012, blogger David Brothers did an amazing bit of investigative journalism detailing the appearance of a number of Marvel titles that had been reverse-engineered from PDF to CBR.68 “The new hotness,” he writes, “are digital scans. Common sense suggests that the scanners take the digital comics themselves, strip them out of the reader, and then package them up.” In conjunction with David Uzumeri, he conducted an extensive forensic analysis of these “digital scans” (an oxymoronic term that serves as shorthand to indicate digital files pilfered from a production server, reformatted, repackaged and circulated through the channels of the darknet) to determine their origin. He concludes, “Marvel closed the hole we found, though I don’t think it’ll lessen how often or easily Marvel’s books can be pirated, except in a few very specific instances. This was one hole that was very easy to exploit. There are others that are completely unavoidable.”69 As unauthorized comic book scanning begins to transform into something more agressive, potentially involving digital trespassing and the theft of files from corporate servers, the amount of time available to study this cultural economy is rapidly coming to a close.
Given these difficulties, why bother to study the circulatory economy of comic book scanners at all? First, there is a hole in the literature around piracy regarding comic book studies. The sole paper we’ve been able to locate on the subject, J. Richard Stevens’ and Christopher Edward Bell’s “Do Fans Own Digital Comic Books? Examining the Copyright and Intellectual Property Attitudes of Comic Book Fans,” analyzes the discourse of readers of unauthorized comic book scans about their motivations for reading them. This is a valuable paper, but it but says little about either the materiality of these scans or the circulatory practices surrounding them. This lacuna is a direct result of the authors making methodological choices to insulate themselves (justifiable, given the fear and uncertainty around freedom of academic thought today). “Because downloading violates copyright,” they write, “the authors sought a methodology allowing free exchanges without fear of reprisal” … though reprisal from whom (comic book scan readers or enforcers of copyright law) remains unclear.70 We believe that our approach makes a valuable contribution to the discussion without necessitating the handling of any potentially infringing materials whatsoever, and is potentially useful to anyone wishing to study circulatory economies that skirt or flout questions of law and ethics.
Second, as Adrian Johns details, virtually everything “we ‘know’ about piracy – its rates, locations, costs, and profits”71 is what is transmitted to us via an assemblage he refers to as “the intellectual property defense industry.” Originally a disparate collection of in-house and trade-specific initiatives, this assemblage began to recruit “people, devices and practices” from law enforcement and the military in the 1970s, and by the 1980s, also included multinational trade organizations.72 By the first decade of the 21st century, it was “a huge and multifaceted enterprise[. A]ntipiracy policing combines the interests and reach of states, corporations, multinationals, and world bodies. Taken in the round, it effectively shapes intellectual property in countless mundane settings.”73 Johns notes that while it is frequently difficult to discern when the intellectual property defense industry acts in the public interest from when it acts in the private interests of its constituents, this boundary may be necessarily fuzzy because its success depends on knowledge that comes from personal, local, and nonprofessional sources.74
Alexander Dent concurs, arguing that piracy is becoming central to neoliberalism itself. If we want to understand the transformations that are occurring in economics, law, and governmentality, and what forms of subjectivity will be available to citizens who regularly make, circulate and consume all sorts of objects, we need to better understand both piracy proper and the various new phenomena that people have described as piracy.75 The current crisis in the intellectual property system is effectively a crisis in late modernity/postmodernity itself, and therefore a crisis that could result in a transformation of our entire cultural logic. Any attempt to resolve that crisis “would have to begin with a similarly informed inquiry into the prevailing practices at stake, and especially into how they change from place to place and develop over time.”76 It’s not simply that academics can’t rely on what the intellectual property defense industry tells us, but that the act of describing popular processes of cultural circulation in detail, infringing or otherwise, will be a necessary part of establishing whatever cultural logic comes next.
Snapshot: Circulatory Practices of Comic Book Scanning Groups in 2010
The ongoing project that produced this paper concerns all aspects of the circulatory practices around unauthorized comic book scans: their social organization; their editorial and production practices; their visual aesthetics; the trajectories that scanned comics follow and how their media and formats are transfigured during the process of circulation; and the circumstances of their reception, including legal and policy questions. We’ve outlined a theoretical framework that will allow us to detail the relationships between the circulatory practices and format choices of comic scanning and culture at large, provided we can support that framework with the necessary mix of qualitative and quantitative data. Accordingly, we’d like to present some preliminary results from the quantitative components of our work to date, dealing specifically with the year 2010, because it is the first year for which we have a full set of weekly records. These results demonstrate that it’s perfectly feasible to conduct digital humanities research without large budgets or access to specialized hardware and software (as pleasant as that would be). We’ll conclude this paper with a consideration of some of the ethical questions that arise when studying digital objects that potentially infringe on the copyrights of others, in order to address questions about what constitutes fair dealing in online academic research.
Over the past year, we77 have been working to ground our research by collecting a specific kind of digital document: descriptor files for torrents of “weekly scan” comic book packs. These descriptor files contain no actual comic book scans themselves; they are simply pointers to existing torrent swarms where the content of the torrent (in this case, the comic book scans) is stored collectively by everyone currently connected to the swarm. These weekly scan packs are assembled from the work of members of the largest comic scanning release groups by third parties (i.e. not, as far as we can tell, by members of the release groups themselves) and uploaded to websites called “trackers” that serve as bulletin boards for currently operating swarms (The Pirate Bay is the most infamous of these). By systematically searching the archives of various popular tracker sites, we have located descriptor files for weekly scan packs almost every week from 2005 to the present. Earlier data exists, but is spotty. With an average of 60 or 70 comics per torrent, that gives us a dataset with about 25,000 records. The most recent version that we have of THELIST, the textfile that the comic book scanning community maintains which contains the titles of all known scans, has around 28,000 lines in it. Many of the lines of THELIST refer to multiple issues of each comic book title, so our dataset is reasonable, but remains an approximation. There are many kinds of comic book torrents, organized according to principles other than weekly releases (writer, artist, series, character, “Day Zero” releases, etc.; there are even torrent series that attempt to present the entire historical output of Marvel and DC). We chose to focus on the weekly release packs because they provide a sense of the regular, cyclical activity of the scanning economy over more than half a decade. The combination of quantitative and qualitative data has already proven useful, furnishing us with the ability to check the claims of the few scanners who have conducted online interviews about their former activities.78 In some respects, the qualitative data supports the claims in the interviews, but in others, there is a substantial difference between the scanners’ claims and what our numbers suggest.
Like phone phreaks, warez teams and online gaming clans, scanners organize themselves into collectives. In interviews, scanners themselves usually refer to the overall assemblage as the “scene” (sometimes capitalized as the “Scene”),79 the collectives within the scene as “groups,”80 smaller working units within groups as “teams,”81 and individuals as “scanners,”82 so that’s the nomenclature we’ve adopted. Scanners do occasionally refer to their colleagues as pirates, but usually in the abstract (“the pirates,” or “pirates are”).83 Digital Comics Preservation, or DCP, is the oldest and most consistent group; the Minutemen is their chief rival. (We’re also looking at the activities of CPS, the most prominent of the smaller groups, and a handful of independents, but focus on the two large release groups here.) According to the scanner interviewed by Jim Mroczkowski in 2011, the rivalry between these groups was substantial around the time of our focus: “At one time, there was a real effort to completely cover all comics that came out (and we succeeded a few times). But now, it seems like it’s more of a virtual pissing contest to see who can get out as many books as possible as quickly as possible. The groups often hurl insults and try to sabotage other groups.”84 An individual self-identified as “Scanbug” suggests that rivalries also occur within groups: “The very short time I was with the Minute Men, The amount of ‘office politics’ or ‘highschool drama’ caused by certain scanners put me off both of the larger groups.”85
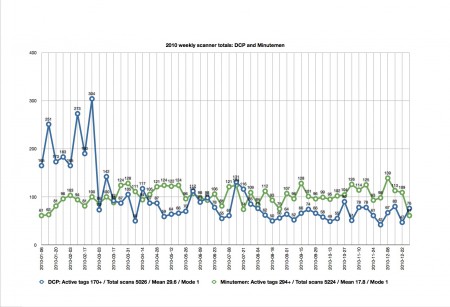
2010 is the first year that the Minutemen start appearing in the weekly torrent packs as an independent release group, with an output rivaling that of the much older DCP. From the information that we have gathered, 2010 also represents the peak of production for both crews (the Minutemen produced about 1000 fewer files in 2011 than they did in 2010, and DCP produced almost 2000 fewer files in 2011). Toward the end of 2012, signs of the Minutemen’s production disappear almost entirely from the weekly release packs. We can hypothesize that because of the increased attention from the intellectual property defense industry to piratical activities on both the open portions of the Internet and the darknet, these activities will, at least, become more difficult to track, as any remaining scanners seek ever-more transient and surreptitious distribution methods. Ironically, the least visible mode of distribution for the foreseeable future may be the circulation of files on removable storage media through the postal system.86
In 2010, approximately 205 active DCP members show up in our data, while we can identify approximately 315 Minutemen. These numbers are significantly in excess of the estimate that the prominent scanner Archangel made of “well over a 100” active scanners in his 2012 interview with Rich Johnston;87 the anonymous scanner interviewed by Jim Mroczkowski provided the same figure the previous year.88 We say “approximately” because our count refers to the number of unique scanner aliases in the weekly release pack indices, and not necessarily to the actual numbers of individuals involved. Mroczkowski’s interviewee states that a scanner may use more than one alias, even in a single pack or from month to month: “I used several different scanner identities over the years […] I honestly forget some of the books I’ve done or identities I’ve used.”89 Mroczkowski’s interviewee asserts that “Most groups work with a team of a scanner who supplies the ‘raws’ and an editor who uses Photoshop to tweak and join double page splashes, adjust colors and contrast and package the images up for a reading program.”90 Our findings corroborate this claim, because portmanteau aliases appear in the descriptor files that are most likely conflations of current individuals’ active aliases (e.g. Minutemen scanners “Darth” and “Piccolo” might on occasion scan together under the moniker “DarthPiccolo”). We also know from both our own research and from interviews that scanners frequently move between groups; this is one of the occasions on which scanners choose a different alias. Even variations in spelling may contribute to changes in our findings (for example, whether or not this is the choice of the scanner or the distributor, DCP scanner “Aquila” is probably also “Aquilia,” and Minutemen scanner “D.T. Rocafella” is missing a space in a few instances, becoming “D.T.Rocafella”). Interestingly, our findings suggest that a number of scanners also take on “corporate” identities, similar to the portmanteau names mentioned above. Where we use “portmanteau” to refer to the mashing-up of two scanner names, we use “corporate” to refer to instances where we suspect a single scanner regularly uses a set of variations of an alias, creating a sort of brand for their identity as a scanner. For example, the DCP scanner “Team” bears a corporate resemblance to “TSTeam,” “Team Second Class Citizens,” and “SCC.”
Every scanner interview we have encountered describes scanning as a collaborative process, involving scanners, editors and distributors. Our research adds more detail to this picture, indicating that team-ups occur both within and across groups. Out of the 5235 files in our data that were produced by Minutemen scanners in 2010, the descriptor files state explicitly that 549 of these were produced by more than one scanner, 19 by more than two scanners, 14 by more than three scanners, and five by more than four scanners (other files may also have been collaborative efforts, but do not necessarily provide credits for the participants beyond the primary editor). Comparatively, DCP members favoured team-ups twice as frequently as Minutemen in 2010, with 1069 files produced by more than one scanner. However, in our sample, there were no explicit instances of more than three DCP scanners on a team, and there are only 45 files produced by three scanners. In terms of cross-group collaboration, we found approximately 49 files created by participants from both DCP and Minutemen. DCP also collaborated with members of CPS just under a dozen times. A small number of scanners (nine in total) listed affiliation with both groups over the course of the year.
The publication years of the files in our 2010 data also suggests an ideological divide between the two major groups. Though it’s common for the publication year to be missing from the descriptor files (11 files uploaded by Minutemen were missing their publication dates, as were 668 from DCP), it’s standard practice for scanners to note the publication year of the uploaded file. This provides us with a convenient way of tracking contemporaneity among uploaded files. There is in fact a sharp divide in focus between the two groups. Digital Comics Preservation placed a great deal of emphasis on scanning older comics in 2010; of the files with listed publication dates, the majority of comics in our sample were from before the year 2000. However, 35% of the 5306 total files were contemporary (with publication dates listed as 2010 or 2011). For the Minutemen, the opposite appears to be true. 78% of the 5235 files in our 2010 sample were contemporary (i.e. up to the “minute”). Moving backward through the publication dates, we see the same trend: over the course of the year, the weekly packs contain 765 scanned comics from between 2000 and 2009 produced by Minutemen members, while there are only 442 titles attributed to DCP from this decade. There are 810 DCP scans from the 1990s, compared to Minutemen’s 244 scans. For titles from the 1980s, there are 839 DCP scans and only 26 from Minutemen. For titles from before 1980, only 44 were scanned by Minutemen (with nothing from before 1960). The packs contain 686 DCP scans from before 1980, dating back to the 1930s.
One of the more nebulous aspects of this type of research regards distribution – how these files reach their intended (or unintended) audience. Whether scanned by individuals or groups, all of the files in the weekly torrent packs are uploaded by individuals not explicitly connected to any crew, and who are not necessarily involved in the practice of scanning. In interviews, the scanners refer to them as distributors,91 and they number in the dozens rather than hundreds. Most of the descriptor files in our sample come from the following tracker sites: The Pirate Bay, Kickass Torrents and 1337x.org. Distributors do not necessarily affiliate themselves with any one of these tracker sites in particular. We suspect that distributors also use corporate aliases, uploading the same information to multiple sites every week under multiple related aliases. For example, the uploader “Ace0801” on 1337x.org may also be “AceOfKnaves0801” on Kickass Torrents and “Joker0801” on The Pirate Bay.92 All three aliases are traceable to one Twitter account, which speaks in the first-person singular while still maintaining the Twitter user’s anonymity.
Distributors create a noticeable bottleneck between scanners and readers. When they’re active, they tend to be prolific and highly organized. When one distributor goes out of commission for whatever reason, another takes up the torch. From January to July of 2010, for example, DCP’s uploads were handled by “espurious,” then taken over by “BFTB” until late September, and then largely handled by “AceOfKnaves”/”Joker0801”/”Ace0801” until the end of the year (with one week handled by “ACBG”). Based on the organized nature of distributor activity, it would appear that they constitute another circulatory network around that of the scanner and release groups. From our data, we can’t tell how much communication occurs between uploaders, or between uploaders and scanner crews, and the existing interviews are vague on this topic. We should note here that all of our research is circumstantial, as we did not perform comparative analyses between BitTorrent tracker sites. This kind of information is incredibly difficult, if not impossible to chart; the circulation of weekly packets on the Internet is untraceable. A packet may be uploaded to one tracker site by one distributor, downloaded by someone else entirely, and then re-uploaded to a totally different BitTorrent tracker. Each upload creates new seeding and leeching swarms and a subsequently untraceable network of distribution.
In our sample, the total output of Minutemen and DCP for 2010 are comparable, with Minutemen producing 5235 files, and DCP, 5306 files. Their output patterns mirror each other from week to week and month to month. However, there are some interesting deviations. For instance, Minutemen’s output grows steadily over the course of the year (from around 61 files a week to 103 files a week). Given that 2010 is their first major year of operation, this likely indicates growing expertise, and increasing communication and coordination within their ranks. DCP experiences a tremendous spike in output at the beginning of 2010, with the highest number of scanned files reaching 304 in the last week of February. Minutemen’s highest number of scanned files in a week is only 139. The Minutemen scanners work at a slow and steady speed, outperforming DCP week-to-week on average, but never approaching anything near DCP’s highest output in a week. However, DCP’s spike is an excellent example of how we should not necessarily take weekly numbers of output as an indicator of group activity. Our data shows that most of the files scanned during DCP’s spike were scanned by one or two “super-actors.” For example, during the week of the 24th of February, DCP’s most productive week, nearly 100 consecutive scanned issues of Action Comics were produced by an anonymous scanner, and 123 files were contributed by “Aquila” (as either a primary or secondary scanner). This is indicative of a more general trend — that is, a minority of individuals do the majority of comic book scanning. While the mean number of scans in 2010 is 29.6 for DCP and 17.8 for Minutemen, the mode for both crews is one. This means (remembering that people may be changing aliases or using multiple aliases concurrently) that a majority of scanner aliases are only credited with scanning one file over the year, and a few super-actors hit numbers in the high triple figures and low four-figures. Almost half of DCP’s files for the year are attributed to only nine scanners. Meanwhile, in the Minutemen camp, almost 1200 of the 5235 total files in 2010 are associated with a single alias (corporate or otherwise): “DTs.”
The fact that most scanners only release one or two files a year may indicate any number of possibilities. Some of these stats can be attributed to scanners changing aliases as they become more prolific, and to simple spelling permutations in aliases. It also may imply a high rate of turnover among the ranks; many scanners appear to try the activity once and then move on. As for the patterns that emerge from the output of both groups, we can speculate that DCP’s activity spike in the first two months of 2010 may have been the result of leisure time over the holidays. Both groups experience a late summer lag; the cause for this might be as simple as people not wishing to spend summer months labouring over a hot scanner, but any number of other explanations are possible. Again, the lack of traceability of these activities, and the secrecy of the actors involved, means that we can only hypothesize about this issue. Nevertheless, a minimum of data-gathering and straightforward analysis usefully allows us to do more than simply take the claims that scanners make in their interviews on faith, and to fill in some details about an otherwise murky cultural economy.
Conclusions
The point of this research is to gain some insight into the politics of the circulation of unauthorized digital copies of copyrighted media in contemporary culture. It’s safe to say that any cultural form that can be copied and shared digitally has developed some sort of informal circulatory network around it, though some of these networks are more robust than others. Accordingly, the research around some of these networks (the circulation of digital copies of TV shows and movies, and especially the circulation of music) has been developed to a much greater degree than the literature around comics. We were curious about whether the circulatory networks around digital comics were different in nature as well as in magnitude. What we’ve begun to see is that through there are similarities between comic scanners and the people that copy and circulate music online, for example, scanners act differently, and imagine themselves differently. Stevens and Bell quote Marvel Comics Publisher Dan Buckley’s observation that the comparison of digital comics to digital music is a poor one, because on the consumption end, listening to digital music isn’t very different than listening to analog music, but that reading a digital comic is a totally different experience than reading a print comic.93 Though scholars of listening such as Jonathan Sterne would very likely disagree with this contention, it’s arguable that print comic culture at least was historically organized around the possession of specific physical objects to a greater degree than music culture,94 and that most readers of comic scans don’t consider their folders of digital files to be a “collection” in the same sense as print comics.95 Our sense is that implication in one of these networks means something different for different subjects involved: not just for scanners and readers, but also for comic book authors, publishers, and even the academics studying such networks.
As Bruno Latour makes quite clear, researchers help to bring these networks into being by writing about them: “any study of any group by any social scientist is part and parcel of what makes the group exist, last, decay, or disappear.”96 So we bear a large degree of responsibility for choosing to write about this subject, and choosing to research it in a particular manner. Part of the motivation for this project is our dissatisfaction with the way Douglass, Huber and Manovich dealt with a similar set of objects. In addition to the aspects of “Understanding Scanlation” we’ve already discussed, its method raises questions about the nascent subject of digital humanities research ethics, especially in the context of team-based research. Working with students on material that exists because of copyright infringement requires extra diligence. Our choice to focus on BitTorrent descriptor files arose from the decision to not place students in a situation that would ever necessitate actually handling potentially infringing scanned comic files. We see this as the middle ground between Stevens and Bell’s position and Douglass, Huber and Manovich’s position. There is a lot of maneuvering room along this spectrum, but the big question is, are the concepts of fair dealing (in Canada) and fair use (in the United States of America) robust enough to support a claim that the academic study of a million scanned manga pages falls under their rubric? Where will university Research Ethics Committee policy fall on such issues? And what would happen if the dataset was a million Marvel and DC pages?
Writing about the circulatory practices of comic scanners and the scans themselves points to another meta-issue for scholars, having to do with the relationship of these materials to the memory institutions of higher learning and their policies for storage and circulation, especially as they relate to copyright laws. By virtue of their differential nature, objects like digital comic scans will always be excluded from libraries, special collections and archives; they constitute a kind of invisible literature. Moreover, most of the intriguing aspects of these objects are precisely related to the non-official version of the things they supposedly duplicate, only found outside of libraries. In “The Canadian Public Domain: What, Where, and to What End?” Carys Craig argues, following Ronan Deazley, that a use-based approach to the public domain suggests that it actually contains not only inchoate ideas and works that have fallen out of copyright, but also any use of parts of copyrighted works for which permission is not required, including fair dealing, educational exceptions, and uses of insubstantial parts of works.97In other words, there may be parts of a copyrighted object, or an infringing object, that fall in the public domain or whose creation can be classified as transformative uses, especially when being studied. Here we’re thinking specifically about the few modifications that scanners make to the comics they scan, such as the signature pages of scanners and groups; these will be the subject of another upcoming paper from our larger research project.
The positions of authors and publishers within this assemblage also merits further thought. Most of the extant accounts of the interactions of comic creators and scanners are narratives of repentance: author has a heart-to-heart conversation with scanner, and scanner repents of their ways. For example, “Archangel” says, “It wasn’t until after a long conversation with a comic creator for Vertigo that made me take a long look at what I was doing and why I was doing it. So I made the decision it was time to stop.”98 When presented as a form of direct dealing, then, the opinions of cultural creators can and do have an effect on scanners and circulators of files. The central axiom of the now-venerable Cluetrain Manifesto was that “markets are conversations.”99 What this means for authors is that direct engagement with one’s audience is now a necessary part of the job. Several decades of transmedia and its attendant participatory culture100 have created the expectation among audiences that they’ll be able to interact with the fictional worlds they adore, and even sway the activities of their creators. Even publishers have gradually come to the realization that scanners and pirates can at least indicate the presence of an untapped or excluded market. In their discussion of digital media piracy and informal economies in the global south, Lawrence Liang and Achal Prabhala write that “it is not just the consumer in the south who needs the informal economy: it is sometimes, also, the artist and the copyright industry.”101 There have been instances around the globe of publishers and authors allowing unauthorized copies to circulate as a deliberate distribution strategy. In such cases, scanners and pirates are enlisted as part of the corporate advertising and public relations divisions.
Liang and Prabhala’s work is important because it serves as a pointed reminder that “piracy” means different things in different parts of the world. They describe “piracy as an organic market reaction to the exclusion of consumers by copyright industries,”102 positioning it not as an act of the privileged, but of the globally marginalized. They also point, indirectly, to the limited usefulness of methodologies that rely on content for their analysis of scans and similar objects (whether powered by supercomputers or hand-tagging). The whole notion of “transformative use” (using a portion of a copyrighted object in a way that produces a new work) in North American copyright law depends on a very specific relationship to information. In many countries in the global south, issues having to do with the unreliability of infrastructure are more immediate than questions about content. “It would, therefore, be insufficient to analyse piracy solely from a content perspective, and it might be valuable to look, instead, at the ways in which piracy facilitates the lowering of the costs of technologies,” write Liang and Prabhala. “It is difficult to speak of ordinary people becoming content producers without also considering that changes in the means of production of culture might be a necessitating factor.”103 In such a context, “(apparently non-transformative) acts of piracy … have much in common with the aspiration to create a more plural, more diverse public sphere of cultural production and participation.” Instead of worrying about what piracy is, in other words, we should be thinking about what piracy does.104 At this stage in our own research, information about where our scanners come from is limited because of the nature of our data corpus. We can tell that the scanning scene is global, with examples of scans appearing from France, Italy and the Philippines, among other locations, but we suspect that the majority of the scanners in our sample are North American.
If so, how effective is comic scanning at fighting the “global copyright hegemony”?105 Stevens and Bell argue that “the scanning and downloading of comic books potentially threatens the principles of capitalistic exchange”106 but we think that if this was potentially true at one point, it now overstates the case. Comic book scanning does not precipitate a crisis that transforms the current social order into something else. In our larger data set, comic scanning is actually showing signs of waning. Recent reports out of Norway show signs of the collapse of music, TV and cinema piracy as cheap, easy-to-use legal alternatives become established.107 Perhaps comic scanning in the form that it existed for the first decade of the 21st century is an example of one of Raymond Williams’ “pre-emergent” forms108: a tool that might be more effective when (or if) picked up by different hands.
Brian Solis, “The State of the Blogosphere 2010,” Altimeter Group, http://www.briansolis.com/2010/12/the-state-of-the-blogosphere-2010/.__
Over the last few years, the metaphor of curation for such online activities has grown in popularity by magnitudes, even as it has sparked a considerable amount of debate about its appropriateness. ((“You Are Not a Curator,” New Curator, http://web.archive.org/web/20100714180425/http://newcurator.com/2010/03/you-are-not-a-curator/ ; “The Editor and the Curator (or the Context Analyst and the Media Synesthete),” Tomorrow Museum, http://web.archive.org/web/20110201164556/http://tomorrowmuseum.com/2010/03/28/the-editor-and-the-curator-or-the-context-analyst-and-the-media-synesthete/; Marco Ament, “I’m Not a “Curator,” Marco.org, http://www.marco.org/2012/03/12/not-a-curator.__ To better understand why this subject might be controversial, try substituting the words “comic scanner,” then “pirate,” for “curator” in the paragraph above and see how it affects the sense.
In a 2012 interview with The New York Times, Maria Popova, the proprietor of Brainpicker, a popular curatorial weblog, described herself as an online “curator of interestingness”. What’s noteworthy about the Times piece is that even as Popova is describing the Internet as a place of “radical discovery,” she is proposing a “Curator’s Code” consisting of two Unicode characters which can be used to indicate the provenance of the things that online curators have located. ((David Carr, “A Code of Conduct for Content Aggregators,” The New York Times, 2012. ↩
Carr, “A Code of Conduct for Content Aggregators.” ↩
Bruce Sterling and John Lebkowsky, “Topic 459: State of the World 2013,” http://www.well.com/conf/inkwell.vue/topics/459/State-of-the-World-2013-Bruce-St-page07.html. ↩
“Content ID,” YouTube, http://www.youtube.com/t/contentid. ↩
Jeremy Douglass, William Huber, and Lev Manovich, “Understanding Scanlation: How to Read One Million Fan-Translated Manga Pages,” Image [&] Narrative Winter 2011 (2010). ↩
Douglas, Huber, and Manovich, “Understanding Scanlation,” 5.) All of this is completely true. The analysis that “Understanding Scanlation” presents, though, brackets these issues for later discussions. What remains amounts to visual studies filtered through a sort of geek machismo. ((Darren S. Wershler-Henry, Free as in Speech and Beer: Open Source, Peer-to-Peer and the Economics of the Online Revolution (Toronto: Financial Times Press, 2002), 189-90. ↩
Neal Stephenson, In the Beginning … Was the Command Line (New York: Avon Books, 1999), 84. ↩
Stephenson, In the Beginning, 84. ↩
Lev Manovich, “One Million Manga Pages,” Software Studies Initiative, http://lab.softwarestudies.com/2010/11/one-million-manga-pages.html.)
It’s worth invoking Mitchell Whitelaw’s warning about the “data mysticism” that underlies the contemporary obsession with impressive digital visualization at this point. Data visualization can provide a sense of data as immanent and material, but it only does so at the expense of the specific attributes of data itself, which is always contingent and relational. ((Mitchell Whitelaw, “Art against Information: Case Studies in Data Practice,” Fibreculture, no. 11 (2008). ↩
Douglass, Huber, and Manovich, “Understanding Scanlation,” 26. ↩
David Hesmondhalgh, “Subcultures, Scenes or Tribes? None of the Above,” Journal of Youth Studies 8, no. 1 (March 2005). ↩
Nick Montfort, “Combat in Context,” Game Studies 6, no. 1 (2006); Ian Bogost and Nick Montfort, “Platform Studies: Frequently Questioned Answers” (paper presented at the Digital Arts and Culture Conference: After Media: Embodiment and Context, UC Irvine, December 12, 2009); Nick Montfort and Ian Bogost, Racing the Beam: The Atari Video Computer System, Platform Studies (Cambridge, Mass.: MIT Press, 2009); Lisa Gitelman, “From Format to Genre: A Note on Documentary Culture,” in Canadian Communication Association 2010 (Montreal: Concordia University, 2010). ↩
Jonathan Sterne, “The MP3 as Cultural Artifact,” New Media & Society 8, no. 5 (2008); MP3: The Meaning of a Format (Durham: Duke University Press, 2012). ↩
Jennifer Daryl Slack and J. Macgregor Wise, Culture + Technology: A Primer (New York: Peter Lang, 2005). ↩
Dick Hebdige, Subculture: The Meaning of Style (London; New York: Routledge, 1979). ↩
Andy Bennett, “Subcultures or Neo-Tribes? Rethinking the Relationship between Youth, Style and Musical Taste,” Sociology 33, no. 3 (1999): 603. ↩
Hesmondhalgh, “Subcultures, Scenes or Tribes?,” 26. ↩
Barry Shank, Dissonant Identities: The Rock ‘N’ Roll Scene in Austin, Texas (Hanover: Wesleyan University Press, 1994). ↩
Will Straw, “Systems of Articulation, Logics of Change: Communities and Scenes in Popular Music,” Cultural Studies 5, no. 3 (1991). ↩
Straw, “Systems of Articulation,” 9. ↩
Hesmondhalgh, “Subcultures, Scenes or Tribes?,” 29. ↩
Hesmondhalgh, “Subcultures, Scenes or Tribes?,” 31. ↩
Steve Neale, Genre (London: British Film Institute, 1980), 19. ↩
Charles Bernstein, “Play It Again, Pac-Man,” Postmodern Culture 2, no. 1 (September 1991). ↩
Gitelman, “From Format to Genre: A Note on Documentary Culture.” ↩
Montfort, “Combat in Context.” ↩
Sterne, “The MP3 as Cultural Artifact,” 826. ↩
Various, but especially Lawrence Grossberg, “On Postmodernism and Articulation: An Interview with Stuart Hall,” Journal of Communication Inquiry 10, no. 2 (1986). ↩
Hesmondhalgh, “Subcultures, Scenes or Tribes?,” 32-33. ↩
Grossberg, “On Postmodernism and Articulation,” 53. ↩
We are indebted to Sandra Gabriele for this observation. ↩
Georgina Born and David Hesmondhalgh, eds., Western Music and Its Others: Difference, Representation, and Appropriation in Music (Berkeley: University of California Press, 2000), 32-33. ↩
Dilip Parameshwar Gaonkar and Elizabeth A. Povinelli, “Technologies of Public Forms: Circulation, Transfiguration, Recognition,” Public Culture 15, no. 3 (2003). ↩
Will Straw, “The Circulatory Turn,” in The Wireless Spectrum: The Politics, Practices and Poetics of Mobile Media, ed. Barbara Crow, Michael Longford, and Kim Sawchuk (Toronto: University of Toronto Press, 2009), 23. ↩
Gaonkar and Povinelli, “Technologies of Public Forms,” 388. ↩
Straw, “The Circulatory Turn.” ↩
Gaonkar and Povinelli, “Technologies of Public Forms,” 391-92. ↩
Marshall McLuhan, Quentin Fiore, and Jerome Agel, The Medium Is the Massage (New York/Toronto: Bantam Books, 1967), 73. ↩
Marshall McLuhan, Counterblast 1954, ed. W. Terence Gordon (Berlin: transmediale/Kulturprojekte Berlin GmbH in cooperation with The GIngko Press 2011; repr., 2011), 13. ↩
John S. Burnett, “Pirates of the 21st Century: Today’s Swashbucklers Wield High-Powered Weapons and Demand Millions in Ransom,” Los Angeles Times, October 4 2008. ↩
For example, see Johnston and Mroczkowski. ↩
In an interview with Rich Johnston, scanner “Archangel” claims, “I bought every book I scanned, including variants when they were available in my area. Any books I edited for another scanner, they had bought. I spend on average between $35-$70 per week on comics, between paper & digital comics.” John S. Burnett, “Pirates of the 21st Century: Today’s Swashbucklers Wield High-Powered Weapons and Demand Millions in Ransom,” Los Angeles Times, October 4 2008. ↩
This is not to say that it isn’t possible to make money from online piracy, as Stephen Chapman argues: Rich Johnston, “An Interview with a Comic Book Pirate,” Bleeding Cool, http://www.bleedingcool.com/2012/04/12/pirate/. As far as we can tell, though, the practice of being a comic scanner or editor doesn’t explicitly involve hosting sites or acting as file locker affiliates, though some may do so under other names or pseudonyms. A currently operating scanner using the alias CCA_Scanner states that one of the differences between the scanning scene of 2009-12 and that of 2004-05 is that now “some people actually make a pretty penny off of the distribution of digital comics, and I don’t mean the comic book companies themselves” Stephen Chapman, “Make Money Online by Selling Pirated Content? These Sites Do.,” ZDNet, http://www.zdnet.com/blog/seo/make-money-online-by-selling-pirated-content-these-sites-do/3660. Nevertheless, comic book scanners and editors distinguish between their activities and those of uploaders and distributors. Every comic book scanner that has been interviewed that we have encountered claims to have bought the majority of the titles they scanned. Archangel claims to have spent $35-70 per week on the comics he scanned (see Johnston). ↩
Timothy Besley and Thiemo Fetzer, “The Welfare Cost of Lawlessness: Evidence from Somali Piracy,” in IAE (CSIC) and Barcelona GSE (Barcelona: Dartmouth University, 2012). ↩
Adrian Johns, Piracy: The Intellectual Property Wars from Gutenberg to Gates (Chicago Ill.: University of Chicago Press, 2009), 14. Location 207. Kindle edition. ↩
Johns, Piracy, 516. Location 6567. Kindle Edition. ↩
Vicky Reich and David S. H. Rosenthal, “LOCKSS: A Permanent Web Publishing and Access System,” D-Lib Magazine 7, no. 6 (2001), http://webdoc.sub.gwdg.de/edoc/aw/d-lib/dlib/june01/reich/06reich.html. ↩
Julia Martin and David Coleman, “Change the Metaphor: The Archive as an Ecosystem,” JEP: The Journal of Electronic Publishing 7, no. 3 (2002), http://quod.lib.umich.edu/cgi/t/text/idx/j/jep/3336451.0007.301/–change-the-metaphor-the-archive-as-an-ecosystem?rgn=main;view=fulltext. ↩
Johns, Piracy, 11. Location 165. Kindle Edition. ↩
Johns, Piracy, 13. Location 187. Kindle Edition. ↩
Gaonkar and Povinelli, “Technologies of Public Forms.” ↩
Owen Chapman and Kim Sawchuk, “Research-Creation: Intervention, Analysis and ‘Family Resemblances’,” Canadian Journal of Communication 37, no. 1 (2012). ↩
“September That Never Ended,” in The Jargon File, ed. Eric Raymond (catb.org). ↩
Giganews, “How Many Newsgroups Will I Find on Giganews? How Long Are Articles Available?,” Giganews.com, http://www.giganews.com/support/usenet/. ↩
Panic, “Unison: The Best Usenet Browser,” panic.com, https://www.panic.com/unison/. ↩
Bryce Roberts, “Web 2.0 Ends with Data Monopolies,” Bryce Dot VC, http://bryce.vc/post/20515719397/web-2-0-ends-with-data-monopolies. ↩
John Battelle, “On the Future of the Web 2 Summit,” John Battelle’s Searchblog, http://battellemedia.com/archives/2012/04/on-the-future-of-the-web-2-summit.php. ↩
Peter Biddle et al., “The Darknet and the Future of Content Distribution” (paper presented at the ACM CCS-9 Digital Rights Management Workshop 2002, Washington, DC, November 18 2002). ↩
Josh Sunderman, “Life, the Universe, and Everything,” The College Hill Independent, http://students.brown.edu/College_Hill_Independent/?page_id=2373. ↩
Kent Walker, “Making Copyright Work Better Online,” Google, http://googlepublicpolicy.blogspot.ca/2010/12/making-copyright-work-better-online.html. ↩
For a detailed discussion, see Ernesto, “Google Adds Pirate Bay Domains to Censorship List,” TorrentFreak, http://torrentfreak.com/google-adds-pirate-bay-domains-to-censorship-list-120910/; “Google Starts Censoring Bittorrent, Rapidshare and More,” TorrentFreak, http://torrentfreak.com/google-starts-censoring-bittorrent-rapidshare-and-more-110126/. ↩
Siva Vaidhyanathan, The Googlization of Everything (and Why We Should Worry) (Berkeley: University of California Press, 2011). ↩
Sybille Krämer, “The Cultural Techniques of Time Axis Manipulation: On Friedrich Kittler’s Conception of Media,” Theory, Culture & Society 23, no. 7-8 (2006): 99. ↩
“The Pirate Bay Trial,” Wikipedia (Wikimedia Foundation, 2009). ↩
“Megaupload,” Wikipedia (Wikimedia Foundation, 2007). ↩
See the note added to the front page of UVRX, a Web search engine with specialized filters for for Badongo, 4Shared, Depositfiles, Zshare, Taringa, Mediafire and Usenet: “Unfortunately it seems that Mediafire have succumbed to the pressure and are now adding the noindex meta tag to files that uses upload as well as all files already on their servers. This means that as search engines recrawl the pages that have the “noindex” tag added, those pages will be dropped from the search engines index. Which means that within the next day or two, no results will show up when searching mediafire. Sorry for any inconvenience, but there is nothing I can do about it. Its actually a bold move by Mediafire, because they will lose a lot of traffic and therefore income, because of it. I assume they were pressured into doing it. And after the unfair treatment Kim Dotcom has received over MegaUpload, I can’t really blame them.” James Watt, “Uvrx: Mediafire Search,” UVRX.com, http://webcache.googleusercontent.com/search?q=cache:xMLThbWgiXIJ:www.uvrx.com/mediafire.html +&cd=2&hl=en&ct=clnk&gl=ca&client=firefox-a. ↩
Harold Adams Innis, Empire & Communications, New ed. (Victoria, B.C. ; Toronto, Ont.: Press Porcépic, 1986), 196. ↩
Along with CBZ, CBR is the comic book scanner’s file format of choice. A later paper from this research will deal exclusively with the editorial practices of comic book scanners. ↩
David Brothers, “Are They Scanning Marvel’s Comics from inside the House of Ideas?!,” 4thletter.net, http://4thletter.net/2012/02/are-they-scanning-marvels-comics-from-inside-the-house-of-ideas/. ↩
J. Richard Stevens and Christopher Edward Bell, “Do Fans Own Digital Comic Books?: Examining the Copyright and Intellectual Property Attitudes of Comic Book Fans,” International Journal of Communication 6 (2012). ↩
Johns, Piracy, 499. Location 6342. Kindle Edition. ↩
Johns, Piracy, 498. Location 6327. Kindle Edition. ↩
Johns, Piracy, 498. Location 6336. Kindle Edition. ↩
Johns, Piracy, 500. Location 6357. Kindle Edition.__ And this is the crux of the matter:
The point is that those problems are not problems of intellectual property narrowly construed. They are, in fact, among the core issues of traditional political theory and practice: issues of privacy, accountability, and autonomy. That is why it was worth tracking the history of the enforcement enterprise back all the way to the seventeenth century and the origins of modern political order. ((Johns, Piracy, 507. Location 6449. Kindle Edition. ↩
Alexander S. Dent, “Piracy, Circulatory Legitimacy, and Neoliberal Subjectivity in Brazil,” Cultural Anthropology 27, no. 1 (2012). ↩
Johns, Piracy, 515. Location 6562. Kindle Edition. ↩
Darren Wershler, Kalervo Sinervo, and Shannon Tein. We are grateful for the indispensable assistance of Max Stein, who wrote some scripts that greatly facilitated the cleaning and sorting of our data, and Deanna Fong, who helped input that data into spreadsheets. ↩
Rich Johnston, “Another Comic Book Pirate Writes,” Bleeding Cool, http://www.bleedingcool.com/2012/04/16/anothr-comic-book-pirate-writes-2/; Jim Mroczkowski, “Ahoy, Comic Book Pirate!,” iFanboy, http://ifanboy.com/articles/ahoy-pirate/; “The Comic Book Pirate Interviews, Part I,” iFanboy, http://ifanboy.com/articles/the-pirate-interviews-part-i/; “The Comic Book Pirate Interviews, Part Ii,” iFanboy, http://ifanboy.com/articles/the-comic-book-pirate-interviews-part-ii/; “The Comic Book Pirate Interviews, Part Iii,” iFanboy, http://ifanboy.com/articles/the-comic-book-pirate-interviews-part-iii/. ↩
Mroczkowski, “The Comic Book Pirate Interviews, Part I;” Johnston, “Another Comic Book Pirate Writes.” ↩
Mroczkowski, “The Comic Book Pirate Interviews, Part I;” “The Comic Book Pirate Interviews, Part II;” “The Comic Book Pirate Interviews, Part III;” Johnston, “Another Comic Book Pirate Writes.” ↩
Mroczkowski, “The Comic Book Pirate Interviews, Part II;” “The Comic Book Pirate Interviews, Part III.” ↩
Mroczkowski, “The Comic Book Pirate Interviews, Part I;” “The Comic Book Pirate Interviews, Part II;” “The Comic Book Pirate Interviews, Part III;” Johnston, “An Interview with a Comic Book Pirate;” “Another Comic Book Pirate Writes.” ↩
Mroczkowski, “The Comic Book Pirate Interviews, Part III;” Johnston, “Another Comic Book Pirate Writes.” ↩
Mroczkowski, “The Comic Book Pirate Interviews, Part I.” ↩
Mroczkowski, “The Comic Book Pirate Interviews, Part II.” ↩
This is a known practice among formerly active digital file sharers. See, for example, the “Sharoma” website, whose page on the Clash states “I am no longer a trader, but I am happy to send out plain-jane CD-R copies or USB sticks/thumb drives/etc of any and all items listed here.” Sharoma, “The Clash – Bootlegs & Rarities,” sharoma.com, http://www.sharoma.com/clash/. ↩
Johnston, “An Interview with a Comic Book Pirate.” ↩
Mroczkowski, “The Comic Book Pirate Interviews, Part II.” ↩
Mroczkowski, “The Comic Book Pirate Interviews, Part I.” ↩
Mroczkowski, “The Comic Book Pirate Interviews, Part II.” ↩
Mroczkowski, “The Comic Book Pirate Interviews, Part III.” ↩
twitter.com/AceOfKnaves0801 ↩
Stevens and Bell, “Do Fans Own Digital Comic Books?,” 766. ↩
J. A. Brown, “Comic Book Fandom and Cultural Capital,” Journal of Popular Culture 30, no. 4 (1997): 26. ↩
Frederick Wright, qtd. in Stevens and Bell, “Do Fans Own Digital Comic Books?,” 752. ↩
Bruno Latour, Reassembling the Social: An Introduction to Actor-Network Theory, Clarendon Lectures in Management Studies. (Oxford: Oxford University Press, 2005), 33. ↩
Carys Craig, “The Canadian Public Domain: What, Where, and to What End?,” Canadian Journal of Law & Technology, no. 7 (2010): 228. ↩
Johnston, “An Interview with a Comic Book Pirate.” ↩
Rick Levine et al., The Cluetrain Manifesto: The End of Business as Usual (Cambridge, Mass.: Perseus Books, 2000), 75. ↩
See esp. Henry Jenkins, Convergence Culture : Where Old and New Media Collide (New York: New York University Press, 2006). ↩
Lawrence Liang and Achal Prabhala, “Comment: Reconsidering the Pirate Nation,” The Southern African Journal of Information and Communication, no. 7 (2006): 111-12. ↩
Liang and Prabhala, “Comment,” 111. ↩
Liang and Prabhala, “Comment,” 112. ↩
Liang and Prabhala, “Comment,” 113. ↩
Laikwan Pang, Cultural Control and Globalization in Asia: Copyright, Piracy, and Cinema, Routledge Media, Culture, and Social Change in Asia (London ; New York: Routledge, 2006). ↩
Stevens and Bell, “Do Fans Own Digital Comic Books?,” 752. ↩
Andy, “Piracy Collapses as Legal Alternatives Do Their Job,” TorrentFreak. ↩
Raymond Williams, Marxism and Literature, Marxist Introductions (Oxford/New York: Oxford University Press, 1977), 132. ↩
Creative Commons Attribution 3.0 Unported License
http://creativecommons.org/licenses/by/3.0/
Image: "Introduction: Paragraph 24”
From: "Drawings from A Thousand Plateaus"
Original Artist: Marc Ngui
https://amodern.net/artist-profile-marc-ngui/
Copyright: Marc Ngui