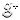Recent work in media studies and by journalists has made it clear that the digital spaces we inhabit are maintained by people who are tasked with sifting and filtering abusive and harmful content. Coining the term “commercial content moderation” (CCM) to describe the largescale, global effort to filter user-generated content, Sarah T. Roberts has brought attention to this crucial labor, an often opaque process that is sometimes viewed as proprietary by social media companies.1 The daily experiences of these workers is not only caught up in confusing and contradictory company policies but is also nightmarish as they are forced to deal with, view, and make sense of graphic content. In fact, their job is so traumatic that YouTube has decided to limit each of them to viewing only four hours of horrific imagery per day.2 The very fact that this work needs to be managed in this way indicates that this labor goes well beyond the verbs we often attach to it. Filtering, sorting, and classifying don’t fully capture what’s happening in these factories of toxicity, since these terms don’t evoke a core part of this labor: interpretation. The moderators that Roberts interviews and the processes that she carefully documents are caught up in complex hermeneutic procedures, since guidelines shift based on geography and platform. In short, this moderation is not “just” filtering since it involves techniques of interpretation, framing, and commentary. In fact, CCM workers oftentimes collaborate with co-workers to talk through their decisions to block or not block certain content.
This process of interpretation demonstrates that moderation requires a constant repetition of harmful, violent, and abusive content, and this repetition wears on those forced to make sense of it. Unfortunately, content moderation workers are not alone in suffering from everything from frayed nerves to PTSD. The very same technological infrastructure that requires this kind of CCM labor also pushes a great deal of responsibility onto users. In fact, the content moderated in these digital sweatshops is often flagged by users themselves, especially those users who are targets of abuse and harassment. Responsibility has been outsourced, and this process has been helped along by a regulatory environment that encourages software companies to take a hands-off approach to moderation.3 Social media companies rely on an infrastructure that pushes moderation on to underpaid workers or unpaid users, meaning that end users and employees of these companies (or the companies they subcontract with) are forced to develop techniques for managing this content. This infrastructure that pushes responsibility outward has actually been decades in the making. In this essay I tell at least part of the story of how we have come to rely on this technological arrangement, one that forces those doing this labor to develop a set of rhetorical techniques for coping with abuse and toxicity. These techniques emerge from some of the deep commitments and ethical assumptions built into our media environments, environments that demand that marginalized people bear the burden of what I will call medium labor, the either unpaid or underpaid labor of those who take care of the channel, manage traffic, and allow for others to communicate.4 In short, medium labor asks certain people to be the medium so that others can use the medium. Our current version of this infrastructure becomes even more complicated as those who are asked to serve as medium laborers are sometimes also end users of the technology. This double duty is evidence of the massive amount of energy that must be spent by marginalized people (most often, black women) in order to manage the channel for themselves and for others.
The management of abusive, harassing, and toxic content requires an entire set of rhetorical techniques, and I focus on one technique in particular since it provides key insights into this broader category of medium labor. That technique is epicrisis, a rhetorical figure that describes the process of citing and commenting on a quotation. Richard Lanham places epicrisis in two different categories of rhetorical figures. First, he suggests that it is an example of rhetorical amplification.5 For Lanham, epicrisis sits alongside rhetorical terms and figures such as apoplanesis (evading the issue by digressing) and divisio (dividing into kinds or classes), and it is but one way of using an existing idea for rhetorical invention, expanding on and amplifying arguments and texts. But Lanham also sees epicrisis as part of a second category, that of “example, allusion, and citation of authority.”6 Thus, he suggests that this technique is both a way of expanding upon an existing text and a way to cite an example or draw upon the authority of another. Epicrisis involves letting the other speak, but it also means pairing the original text with commentary. It stands as perhaps the perfect metaphor for mediation itself. By using epicrisis, the rhetor simultaneously stands outside and within the communication channel, allowing the other to speak but also intervening. The line between medium and message is blurred, and this technique presents us with a moment when the medium shows itself to be the result of layers of labor rather than a “mere” channel.
From content moderators who must cite and then comment on harmful content to Twitter users who quote the abusive tweets and then respond to them, to the telephone operators of the late 19th and early 20th century who were forced to manage the abuse of telephone subscribers, epicrisis is a core technique for those who have long managed our channels. Epicrisis is the titular technique for a category of techniques we might refer to as epicritical. The prefix “epi-” suggests not only that one is commenting upon the words of another but also that epicritical acts operate as a layer that surrounds and protects, like the sheathing of a fiber optic cable. Epicrisis and its sister techniques operate as critique, but they are also “critical” in the sense of being “mission critical.” Without this epicritical labor, our information infrastructure would not be able to operate. What is most important to understand about epicritical, medium labor is that it is not a critical move that operates at a remove from the content, critiquing from above in order to debunk or undo. These epicritical moves emerge as techniques for those less likely to have the ethos to critique from above. Women, people of color, and those in the LGBTQIA community are not necessarily citing passages and commenting only in order to demonstrate mastery. This may be part of the rhetorical dynamic, but it is not the only force at play. This set of techniques is not above or apart from the content that it surrounds and comments on – it is a set of medial moves that make clear what kind of work is necessary to protect and maintain the network. Epicrisis is a technique for managing the lines, and while it may be subversive in certain cases, it is also a survival tactic and, more generally, a fact of life. It is not something one necessarily chooses but rather emerges out of a situation in which certain groups of people are tasked with making the system work.
When content moderators are asked to deal with harmful content, they are asked not just to block it but also to interpret it, to make sense of it. This process is similarly carried out by the users who report bad actors in social media spaces, as they fill out forms and click checkboxes that document harassing tweets and posts. As we will see, this process of epicrisis is even carried out by Twitter users who use the “quote tweet” function to expose the abuse they are experiencing on the platform. However, this technique extends further back historically, and I will argue here that our current communication infrastructure is part of a long history of medium labor being pushed on to marginalized people. From white women in the parlors of the 19th and early 20th Century being asked to manage and “draw out” conversations to those same women being asked to absorb abuse and harassment of telephone subscribers as they worked as operators, to the Black and Hispanic women who were then asked to step into those positions when white women vacated them, the tale of our toxic communication infrastructure is indeed epic scale and centuries in the making.
The epic crisis of online harassment is at least in part the result of an epic tale of an unjust communication infrastructure. I understand this crisis of online harassment (one that is exemplified by coordinated campaigns of abuse such as GamerGate but also takes place in more mundane, everyday ways) not in the sense of an acute moment or event, not the arrival of something brand new that requires a response. Instead, this crisis is one that has continuously unfolded across multiple historical moments and technological arrangements. It has manifested in different ways, but certain features have been persistent, and it has thrived on an infrastructure that relies on unpaid or underpaid (and often invisible) epicritical labor. Wendy Chun has argued that networked technologies thrive on the logic of crisis and that a constant barrage of seemingly acute, brand new crises create a loop between habit and crisis. A crisis arrives, and it disrupts our habits: “as soon as one is comfortable, habits are disrupted, so that one is always dependent on and responsive to the environment. One must constantly respond in order to remain close to the same.”7
However, Chun also sees potential in habit, in repetitions that are always repetitions with a difference, and so she argues that our responses to the crisis-habit feedback loop should perhaps be to inhabit our habits differently, to see them not only as robotic responses or automated subroutines but rather as ethical responses to radical encounters with an other that might even be able to disrupt the feedback loop of repeating crises. Perhaps when Chun argues for the “decoupling of habit from crisis” what she is arguing for is an understanding of how habits become techniques, even if the latter term might imply a kind of free agency with which she would not be comfortable.8 Regardless, this notion of networked technologies thriving on the logic of crisis is crucial for understanding online abuse and harassment because the “crisis” we are currently experiencing is not new or acute, even if it does call for immediate responses. It is a contemporary version of what I am calling an epic crisis, one that has been with us for quite some time.
Epicritical techniques have been an ongoing set of responses to this epic crisis, and they have long served to protect and maintain abusive and unhealthy information systems. By tracking epicrisis across media ecologies and historical moments, we see the labor of maintaining the channel and how certain techniques for doing so persist even as technological change would appear to radically upend how information travels. Here I have chosen to turn to the telephone system in order to track the historical lineage of such techniques. While this set of problems does not begin with the telephone, the telephone and social media networks both participate in the long history of pushing medium labor on to women and people of color. From telephone operators to telephone subscribers, the responsibility of medium labor has long been shirked by the companies that claim to be in charge of our communication technologies. From the telephone, I move to a contemporary example – the use of the quote tweet by Twitter users – in order to demonstrate yet another iteration of epicritical, medium labor. In this instance, targets of abuse are asked to both be the medium and to use the medium, doing the double labor of managing the channel so that large corporations are freed of the expensive and complex work of managing content and so that the vast majority of users are able to use these platforms in relatively friction-free ways. Without the epicritical techniques documented in this essay, our communication systems could not operate.
Nimble Fingers, Soft Voices
A 1912 issue of Popular Electricity features a story about a device for making embroidery patterns. The device allows for the creation of patterns “for pillow tops, doilies and a score of other fanciful creations in which every woman delights.”9 With this new technology, patterns could be created with electricity, partially automating a process that relied on human hands and carbon paper. An electric motor drove a needle that punctured paper and created 20 templates at a time. The machine automated a portion of this process, but it still required human labor (a woman, of course) to guide the needle and create patterns. On the very next page of this same issue of Popular Electricity is a story about how telephone operators in the United States compare to their counterparts in England: “We are prone to look upon time, when waiting, as longer than usual and this is nowhere more evident than when using the telephone. Careful observations show the telephone operator to be quick and efficient.”10 The story documents this quickness and efficiency, giving the American operator the edge when it comes to providing an efficient communication infrastructure for the subscriber. The average time from signaling the operator to the time she answers is 3.1 seconds, two seconds faster than “her English cousin.”
Two time-saving systems, both reliant upon the labor of women, sit on adjacent pages. What do they share? And what might they have to do with digital infrastructures or online harassment? First, the link between this issue of Popular Electricity and the digital has less to do with silicon chips and more to do with digits – that is, nimble fingers. As Elizabeth Cobbs recounts in her study of the telephone operators who traveled to Europe during World War I to manage the switchboards that connected trenches to one another, “women…showed great nimbleness with the multiple jacks, sockets, ringers, and buzzers on the boards of busy switching stations. It was a fast-paced job requiring steady nerves.11 Kenneth Lipartito argues that the job required traits such as “respectable deportment, accuracy, attention to detail, good hearing, and good speech [that] were commonly held to be female…traits.”12 The inventor of the telephone was aware early on that his system required a certain kind of operator and that it actively encouraged bad behavior. In a 1910 address before the Telephone Society of Washington, Alexander Graham Bell described the early telephone exchanges and the trouble with boys:
I remember very well the early telephone exchanges, which were very different from the ones that you have to-day. The noise and the bustle and the confusion in even a small office were very annoying, and there were other disturbing things also. The Operators were chiefly young men or boys. The company got numerous complaints from subscribers that the young men or boys in those central offices would swear over the telephone. In fact, the telephone seemed especially to be designed to propagate profanity. Well, there were not only young men; there were a few girls, and somehow or other the soft voices of those girls served to protect the telephone company. The people at the other end of the line did not like to get the young woman at the central office into trouble, and there were always far less complaints from the subscribers served by the girls than by the boys, and so little by little the girls took the place of the boys, and the telephone has proved one of the great new occupations for women.13
This is a remarkable passage. Bell recalls the story, now told in a number of historical accounts of the telephone system, of the young boys that “talked back” to telephone subscribers, demonstrating that they were not well trained by society for medium labor. Beyond this, Bell describes the telephone’s very design as contributing to the propagation of profanity, a problem that (as we will see below) did not end when telephone exchanges fired the boys and hired women Bell’s discussion of the telephone system’s complicity in profanity is evidence that prior to today’s discussions of digital design contributing to abuse and harassment there was a recognition that communication systems are not neutral tools. Finally, the “soft voices” described by Bell should remind us of the care involved in medium labor. Deploying their more genteel manners, these women were, in Bell’s words, protecting the telephone company. This is an important idea to keep in mind for the remainder of this discussion of medium labor. The work done by women and other marginalized groups across media ecologies is very much about maintaining networks, protecting infrastructure, and doing the work required to ensure that things run smoothly for others. Much of this labor is about managing problems so that others do not have to.
Bell’s comments regarding women telephone operators are indicative of the broader assumptions about gender and technology in the late 19th and early 20th centuries. Women were seen as having the correct temperament for the job of telephone operator. Luckily, for Ma Bell, women of this time period had been taught core skills in the classroom as well as in conduct literature. Nan Johnson’s archival research on “parlor pedagogies” documents the extensive advice women received regarding how to be a medium. The parlor rhetoric movement of the late 19th Century shifted rhetorical education outside of the classroom, providing citizens with tools for becoming orators at home, in the parlor, and at social gatherings. However, if men were encouraged to orate and debate, women were encouraged to facilitate. Parlor rhetoric literature as well as conduct literature for women “make the argument repeatedly that female eloquence can be measured by the degree to which a woman’s voice provides background for other speakers.”14 Johnson points us to an 1896 text called The Glory of Woman, which explains how women were enlisted not as orator but as medium:
It is well that every group should have its leader or centre; not always the one who talks most or best, but the one who listens, manages, suggests and draws out or gives opportunities to others. A lady of tact and intelligence does the best. She guides the conversation…A lady who can do this, not only for a single group, but for a drawing room full of guests…is fit to be a hostess and social queen. If the first qualification for conversation is to know how to speak, it is, in some ways, a more important one to know how to listen. We draw out, encourage, excite, and elevate by our manner of receiving and accepting what one says. The orator gets life, suggestion and support from his audience. He is borne up by the waves of their appreciation. Good listeners make good talkers.15
The lady who learns how to listen more than speak and how to “encourage, excite, and elevate” the speech of others is perfectly positioned to become a telephone switch. Trained to listen and make the connections, she was primed for the job. Epicrisis is a particularly useful tactic for those doing the labor of “drawing out” the ideas of others. Of course, the rhetorical training of women at the turn of the century is a complicated story, and we should note here that the story is not only about docile facilitators staying out of the way. A great deal of research in feminist rhetorical history has demonstrated that women developed techniques for operating from within a patriarchal system that expected them to be silent. Not all of those strategies were as stealthy as those I am describing here. For instance, Jacqueline Jones Royster’s Traces of a Stream documents and analyzes the essays of African-American women in the late 19th Century. Though her study focuses on elite woman (a term Royster uses to account for both economic status and also the status these women held in their own communities), these writings show that epicritical techniques were not the only ones available to women and other marginalized groups during this period.16 Still, much research in feminist rhetorical history demonstrates that “female rhetors have made meaning not by transgressing or resisting their gendered sphere to become rhetors but by speaking within and from this sphere.”17 Historians of rhetoric have thus argued that it is necessary to examine the rhetorical techniques of women and other marginalized groups with a careful eye, examining rhetorical history with an understanding of how these groups negotiate power dynamics. This is the kind of analysis necessary if we are to understand epicritical labor across different media ecologies.
When it came to the telephone system, some of these rhetorical techniques were considered prerequisites for the job of operator. Though it was sometimes considered a “natural” aptitude and not presented as skilled work, operators needed to do more than just connect two wires. As Venus Green argues in Race on the Line, women telephone operators were required to have a certain level of education: “as grammar school and high school graduates who had been socialized to ‘please’ others, female operators achieved literacy and social skills before employment. Afterward, they learned how to use these skills in combination with mechanical switchboard operations on the job.”18 They needed to provide a personalized touch that one couldn’t get with the telephone’s main competitor, the telegraph, a technology often manned by men. Green makes clear that Bell Telephone saw this as skilled labor: “Bell Telephone officials made a distinction between ‘getting people talking’ and simply connecting two wires. In their infancy, telephones competed with the telegraph, the prevalent method of communication at the time, and telephone companies competed for hegemony over the entire business.”19 And perhaps the operator’s training went beyond even grammar school, since women at this time would likely have worked on a needlework sampler, training her nimble fingers in preparation for the switchboard. The connection between needlework and rhetorical education is documented by Maureen Daly Goggin, who has argued that an attention to needlework samplers is of interest to rhetoricians not only because such artifacts contained textual elements (needlework practice often involved the creation of letters, numbers, and phrases) but also because it shows how rhetorical praxis is part of complex material networks, only some of which are best understood as discursive.20
The training of operators extended deep into 19th and early 20th century life, shaping women’s bodies so that they could be plugged into the circuit. To return to the 1912 issue of Popular Electricity, these stories are an indication of the complex and diffuse pedagogies that trained the bodies of women so that they might be deployed as telephone switches. Nimble fingers, a patient demeanor, and a deferential attitude were all prerequisites. The switchboard connects a circuit between the parlor and today’s digital spaces, telling the story of our contemporary digital infrastructure. But these contemporary arrangements are not as frictionless as they appear to some users, and just like the telephone network, they require a great deal of labor that is too often dismissed as rote or mechanical. The disregard for these “mechanical” functions is not just about technological advancements and the automation of certain kinds of labor but also about the attempted erasure and silencing of entire categories of people from our media histories. Online harassment should be seen as part of this complex but fairly coherent strategy for silencing the infrastructure, for keeping the machine running smoothly, and for making every attempt to create a system that does not talk back. The gender dynamics of this are clear, as women are trained to be nimble, patient, and quiet and to bear the burdens of affective labor, and the racial dynamics are clear as well. As Green demonstrates in her study of race and the telephone system, when white women moved on to other professions, people of color (and especially women of color) were called upon for this labor. Where white women might have been allowed to speak up and appear (even if only as a maternal figure who is in charge of keeping the conversation going), black and Latina women are silenced more swiftly. This latter dynamic has been especially visible in telecommunications labor, where “Latinas have worked as invisible information laborers in telecommunications, providing the infrastructure that supports contemporary new media systems.”21
This labor was both skilled and physically demanding, and the protection and maintenance of the telephone network took a toll on the body of the telephone operator. Operators often suffered from abscesses in their eardrums, headaches, and corns on their ears (perhaps prefiguring the mental and physical stress of commercial content moderators).22 This is our first signal of how difficult it was to be a circuit. One key skill was the “ability to gracefully defer,” but operators also needed to manage a complex set of problems and requirements. As calls came in, they reached for a cable with male plugs on both ends (the puns write themselves…), plugged into the subscriber’s line, raised their voice an octave, and asked “Number please?” From here, things got much more complicated. They need to know whether to ring the line loudly (so it could be heard on a factory floor) or softly (in case a baby was sleeping) and how many times to ring the line (in the case of party lines used by multiple subscribers). If it was a long distance call they might need to coordinate with several different offices to make the connection while also managing other calls simultaneously, all while keeping track of call times for billing. All of this needed to be done in a personalized way that made subscribers see, or rather hear, the value of using a telephone rather than a telegraph.
Of course, the physical demands are only part of the story, since operators also needed to be skilled at dealing with the sometimes abusive signals on the line. They were expected to have perfect hearing, and any problems would no doubt result in management receiving calls to: “Take that deaf girl out of the circuit.”23 And the frustration with the ‘deaf girl’ in the circuit was not always expressed to management – it was often directed at the circuits themselves. Turn-of-the-century newspapers report a number of incidents of harassment. When W.A. Woods of Sacramento was connected to the wrong number in 1908, he called the operator to swear at her. The operator had Woods arrested, and a judge gave him the choice of either a $20 fine or 20 days in jail.24 The May 5, 1917 issue of Telephony told the story of Morse M. Frankel (his name suggests that he probably should’ve sent a telegram) who “took delight in using offensive language to operators” and whose service was discontinued. Disconnection was the typical threat and punishment for this behavior, and some companies even installed gramophones in order to record the abuse of operators. While much of this abuse was carried out by men, “society women” were guilty of it as well.25
In 1909, a Texas state representative actually proposed a bill making it a criminal offense to swear over the phone.26 But most thought that this behavior was best addressed by deferential phone operators. H.K. McCann of the New York Telephone Company insisted that there was no need for such a law in New York; however, he did say that operators were instructed to say “number, please” with a rising inflection, in a pleasing way: “Our idea is that courtesy begets courtesy.”27 A Chicago telephone company took this courtesy a step further, inviting South Chicago businessmen who had been “making the wires blue with ‘cuss’ words” to a dinner party. This party indicates an important dimension of the operator’s labor, one that isn’t accounted for if we understand the operator as “mere” medium or passive channel. At that party, the operators demonstrated how the switchboard worked (no doubt revealing that the job was more difficult than imagined). But the party didn’t stop there – the operators also served hostesses, dancing and socializing: “Gertie, the blonde, danced with Hardtax, the hardware merchant, and looking up into his spectacled eyes, remarked sweetly, ‘I could never have dreamed such a nice man as you could say such awful words over the telephone.”28 Everyone left the party convinced that ‘there will be no more swearing over the telephone by members of this association.” The lesson here was taught by the operators, whose patience and nimble fingers moved from the switchboard to the cocktail tray. The epicritical labor was, once again, multimodal and multidimensional, supporting the network and gently correcting those who were causing problems. If telephone operators were taught to diffuse situations, to absorb and redirect energy, men were taught, over and over again, that they could rely on an infrastructure that would cater to them. At times, they even relied on the operator to correct them and keep them in line – Gertie’s gentle correction of Hardtax is epicritical, and she is gesturing toward a strategy that takes various forms even as media ecologies shift.
The Epicritical Labor of Documenting Harassment
As telephone operators gave way to automatic switches, the responsibility for dealing with callers who were “making the wires blue” or that were otherwise abusive began to fall to subscribers. Even in this arrangement, targets of telephone harassment were still called upon to act as medium, and the epicritical skills remain. Though automated switches meant that fewer women were doing the work of connecting the lines, women were still experiencing a disproportionate number of abusive and obscene phone calls. One Canadian Survey estimated that more than 80% of women had experienced “obscene or threatening” calls.29 AT&T recognized that abusive, harassing, and obscene calls were a big enough problem that they needed to provide subscribers with ideas for how to address the problem. A 1969 AT&T pamphlet entitled “What to do about annoying phone calls” insists that AT&T takes the problem of “annoying” calls seriously: “We want to help stop this source of irritation, because we want you to enjoy not only the best, but also the most convenient and pleasant telephone service in the world.”30 The pamphlet establishes three kinds of annoyance calls: sales calls, nuisance calls designed to irritate, and a third category of abusive, harassing, or obscene calls. The pamphlet immediately enlists the subscriber’s help in dealing with this problem, setting a precedent for today’s outsourcing of content moderation and the reliance on end users to report abusive behavior. So, how can the phone subscriber help Bell Telephone? They can remember that they are not obligated to respond to questions, ask who is calling, be firm with salesmen when they’re not interested, investigate suspicious businesses with the Better Business Bureau, and remember that “it’s [their] phone service and [their] time,” meaning they can hang up at any time. Unsurprisingly, Bell is careful to note that sales and surveys by phone are an important part of doing business, even if they want to note that sales calls can bleed into annoyance calls. As for nuisance calls, they note that these do not only come from strangers but also from neighbors and fellow employees. In rare circumstances, they come from “unsupervised youngsters, misguided or frustrated people…[and] the mentally ill.” The pamphlet offers a set of best practices for dealing with sales calls and nuisance calls, primarily focused on using the phone on your own terms and never revealing too much information. All of these suggestions enlist the subscriber in the management of unwanted network traffic.
When it comes to abuse, harassment, threats, and obscenity, the company offers some rules and resources, but they also suggest that any kind of sustained or coordinated campaign requires a call to the police: “If you are unfortunate enough to be a victim of [a sustained] campaign, the rules in this booklet are not enough. Call the police, call the telephone company – immediately.” AT&T has in mind bomb threats, threats to life and property, kidnapping and robbery threats, and threats of bodily injury. For annoying calls that do not fall in this more extreme category, they offer not only the practices I have already summarized but also an “annoyance call log.” This log allows the subscriber to track details about the calls: dates, times, type of call, who was and wasn’t at home when the call happened, description of the caller, and description of the voice.

Fig. 1. Questionnaire provided to subscribers dealing with annoyance calls, included in “What to do about annoying phone calls” pamphlet.
This kind of data and metadata gathering operation aligns with a different meaning of epicrisis – the critical summary of a medical case history. Just as a doctor might offer a critical summary or epicrisis of a patient’s medical condition, the telephone subscriber is asked to offer documentation and analysis of a harassing phone call. The idea of this questionnaire is to get the victim to gather the information and critically evaluate it, and this practice should look familiar to anyone who has decided to report a social media user for abuse or harassment – users are tasked to record not only the act of harassment but also to answer a series of questions about the act.
In the case of the phone call log, they are also asked to cite the offensive act and then interpret it in light of other factors (recent publicity, for instance). This questionnaire also serves as a kind of training device to get the called person to think about the entire rhetorical situation of the harassing call. It even nudges them to begin developing a list of suspects. The task is to annotate, evaluate, and make sense of the problem. Epicritical work is about interpretation and evaluation, and it is about helping those who own the network in their efforts to contain the problem. Like the woman managing the 19th century parlor or the telephone operator dealing with abusive calls, the telephone subscriber in the 1960s is now expected to manage and track things, helping to maintain the system, evaluating and reporting any problems or perhaps trying to address those problems on their own (by hanging up, by being firm with an annoying caller, etc.) before they turn to the phone company or law enforcement.
The phone company wants to gather data and metadata in order to determine what kind of problem they’re dealing with, but they want to do so without listening in on calls, which they thought subscribers would consider an invasion of privacy. Bell telephone did some of its own labor as well, and from early on it was able to trace calls when abuse or harassment occurred. The documentation of the process by which they trace calls insists that there is no “listening in” to the call – they are merely trying to track the call’s origin. Again, we should notice another deep commitment of the system that lives on in today’s networked media: the privacy of harassers and abusers often trumps ensuring the safety and privacy of victims of abuse and harassment. Echoes of the libertarian ideology of contemporary software companies can be heard as Bell Telephone continuously insists that it is not tapping your phone line. A Bell Labs position paper from September 1968 addresses how the company identifies the telephone line being used for phone calls. The paper recognizes that Bell is “usually the only one who can identify the line from which calls originate and that we have an obligation to do so in aggravated cases.”31 It also once again makes clear that what they do is not “wiretapping” and does not infringe on privacy: “We don’t listen in or record conversations.”
In addition, the paper says that the company is often developing new techniques for line identification as equipment changes, but that it avoids “giving details of the techniques used to identify calling lines. Public disclosure of this information can make it easier for annoyance callers to avoid detection.” The position paper describes a number of different ways to identify lines, including the use of a “called-party holding” device that allows subscribers to ask the central office to trace a call, “trouble indicators” that allow for the identification of the trunk line on which the offending call arrives at the central office, as well as a more sophisticated system that “punches out an IBM card with the incoming trunk number, called line number, and time of call.” This last approach was only possible on the newest electromechanical switches, which comprised about 30 per cent of Bell System phones in the late 1960s. Upon identifying the lines, Bell would secure written consent from the subscriber being harassed so that the number of the offending line could be sent to law enforcement. If the “annoyed customer” doesn’t want to take legal action, Bell would be able to, if it chose to do so, discontinue service to the offending subscriber.
Bell’s procedures insist upon the fact that they are not engaging content – they are purely concerned with tracing the call, leaving the more difficult medium labor, the epicritical work of making sense of the content and of abusive behavior, in the hands of subscribers and targets of abuse. Both telephone operators and, eventually, subscribers are relied upon to document, comment upon, and contain this behavior.
The Weavers of Speech
The story of epicrisis continues today in various forms but most interestingly in a debate about Twitter and the use of the “quote tweet.” In June 2018, Charlie Warzel, a former technology writer for BuzzFeed, noticed a prevalence of quote tweets in his Twitter feed. This function was implemented by Twitter in 2015, and it allows a user to embed someone else’s tweet much like they would any other piece of media. That embedded tweet can then be accompanied by a comment – an annotation that responds to the quoted text. It can also mean that the tweet is ripped from its initial context and put toward different rhetorical ends. Warzel argued that quote tweets contributed to toxic exchanges on Twitter, and he saw people using this technique to “dunk on” the opposition, noting that this form of engagement is more about winning a fight than about any kind of “healthy” response.32
Warzel’s tweet drew a response of agreement from Kate Starbird, a design and engineering researcher at the University of Washington. Starbird pointed to a study in which she and fellow researchers had found that while retweets (the sharing of another’s tweet without any additional commentary attached) often remain inside of social media “echo chambers,” quote tweets tended to serve as bridges between those echo chambers. This research team was examining what the study calls “superclusters” of Twitter accounts that have similar audiences, and in this particular study they were studying accounts with very different opinions about the #BlackLivesMatter hashtag.33 According to Starbird, using quote tweets to draw attention to the opposition, pulling them “out of context” and then using them to ask your followers to “dogpile,” is a favored rhetorical tactic that is primarily about conducting “back alley ambushes.”
While the study mentioned by Starbird found that there was a great deal of interaction within superclusters, the researchers did find that quote tweets were likely to involve interactions between superclusters. The quote tweet often establishes a thin thread between dense clusters of tweets that represented conversations amongst those who agree with one another. The study suggested that these quote tweets are “likely not acts of attempted persuasion, but are perhaps intended instead to utilize the visibility of the challenged account to draw attention to the counter-narrative.”34 In other words, a quote tweet is likely to represent a Black Lives Matter activist drawing attention to counterarguments by people from a different supercluster (or vice versa). This discussion of persuasion is of course of great interest to rhetoricians like myself. The assumption here seems to be that persuasive discourse should always aim to change the mind of the opposition, and the quote tweets under discussion are largely not attempting to do this. However, this is only one way of understanding the aims of persuasive speech. For instance, we might understand the quote tweet as epideictic rhetoric, a form of rhetoric that Aristotle described in terms of “praise” and “blame” (such as funeral orations) and that recent rhetorical critics have theorized in more expansive terms.35 Regardless of the working definition of “rhetoric” or “persuasion” undergirding this conversation, Warzel and Starbird are in agreement that the use of the quote tweet to expose an opposing argument is not a healthy approach to debate. Warzel even indicates that Twitter’s design decision to implement the quote tweet is a direct contributor to toxic interactions on Twitter.
A great deal of recent research supports the premise of Warzel’s argument that Twitter’s design decisions can actually contribute to the behaviors of its users. For instance, Sasha Costanza-Chock’s work on “design justice” examines “how the design of objects and systems influences the distribution of risks, harms, and benefits among various groups of people.”36 Design justice understands design both as contributing to problems like abuse and harassment and also as a potential site for addressing those problems. Similarly, scholars such as Safiya Umoja Noble and Cathy O’Neil have examined how the design of algorithms increases inequality.37 And while Twitter’s design decisions about features like the quote tweet certainly do contribute to toxic discourse on its platform, the epicritical labor I have documented in this essay suggests that the quote tweet is part of a long history of foisting that labor onto marginalized communities. The quote tweet is a symptom of a much larger problem – not unhealthy debate but an unhealthy infrastructure that pushes responsibility for content moderation and managing harassment onto those who are other underpaid or unpaid and onto those experiencing a bulk of the harassment.
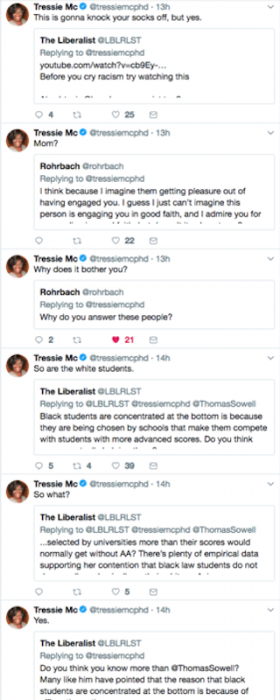
The quote tweet is often a prime example of epicrisis, and it is carried out quite elegantly by public figures such as Tressie McMillan Cottom. McMillan Cottom, a professor of Sociology at Virginia Commonwealth University and best-selling author, routinely experiences trolling, abuse, and harassment online. One of her preferred strategies for dealing with this is the quote tweet (Figure 3).
On Twitter, one can ignore abuse, respond to it, or one share it with their followers, pushing it back out onto the network. McMillan Cottom prefers the latter, quoting the offending tweet and adding a response that is less about resolving the issue and more about attracting the attention of her followers. While Professor McMillan Cottom’s is one key example of someone using the quote tweet in this way, there are plenty of examples of targets of harassment using this same strategy. Roxanne Gay, professor and best-selling author often uses quote tweets to expose abuse and harassment, as does Jemelle Hill, a staff writer for The Atlantic who routinely experiences racist and misogynist abuse. Emily Gorcenski, a Data Scientist and survivor of neo-Nazi attacks in Charlottesville, Virginia, often uses screenshots of abusive tweets in a similar way in order to respond to attacks. These are just a handful of examples, and they are not meant to suggest that every quote tweet serves the same purpose. While a number of users make use of the quote tweet for a range of purposes, the technique described here is often used by those on Twitter that experience a disproportionate amount of abuse and harassment.38
What does such a rhetorical strategy achieve? One might read this as nothing but mockery and an invitation extended to McMillan Cottom’s thousands of Twitter followers to pile on the troll. This is how both Starbird and Warzel understand this technique. However, we should also think of the quote tweet in terms of amplification. First, the quote tweet amplifies in the sense of amplifying sound – the tweet meant for Cottom is amplified, made louder, and spread out to others. The audience is now not one but many, and it reveals the machinations of medium labor to the rest of the network. The quote tweet is saying: “Witness what I have to deal with on a regular basis.” However, we might also think of this in terms of rhetorical amplification, a way of discovering arguments and expanding on an idea. This amplification often involves repetition and iteration, since it aims to turn a phrase or an idea over and explore its possibilities. This is, of course, repetition with a difference – it expands and opens up an existing text or utterance with description or with examples. It also surrounds the initial tweet, repackaging it and reframing it for a new audience. The quote tweet is an amplification that serves a range of purposes. For one, it is a call to “get your friend” – a way of pointing out absurd behavior by those engaging in abusive or harassing behavior. But the quote tweet is also a moment when everyone has to witness that labor that has sometimes been hidden and forced into the shadows. These are moments when we realize that our infrastructures have always been built on the labor of those who are encouraged to be silent in the background.
The quote tweet is a response to the demand that medium labor be carried out in silence. Most importantly, this medium labor is skilled and has been taught and honed in a variety of ways. From nimble fingers to patient ears to epicrisis and the tracking of data and metadata, this is the skill of managing the channel, sometimes appearing and other times blending in. A closer look at today’s media ecology shows that certain people continue to carry out a disproportionate amount of this labor. It is now clear that the once standard advice – “don’t feed the trolls” – is laughable and could only be recommended by someone who hasn’t been tasked with the intense labor of managing the medium. Silence may help with trolls but not with harassers, who are primarily hoping for silence. The quote tweet is an epicritical response that recognizes that silence is not a viable strategy if one wants to deal with the systemic abuse and harassment of women, people of color, and those in the LGBTQIA community. It reveals to others in these spaces that medium labor continues to be unequally distributed in our contemporary media ecologies. Those tasked with this labor rely on epicritical techniques, which serve as de facto network management, dealing with a problem that software companies seem uninterested in dealing with in any thoroughgoing way. These uses of epicrisis to respond to social media harassment offer us a way to understand these techniques as part of the long history of medium labor.
Recall that Stewart et. al. frame the quote tweets as unproductive and as little more than attempts to humiliate the opposition. But these quote tweets often serve as bridges, tenuous connections between clusters of agreement, thin strands spun by those who continually absorb venom and maintain a network with epicritical labor. The quote tweet brings to mind Bell Telephone’s 1915 description of telephone operators as “Weavers of Speech” (Figure 5).
The advertisement features a woman “weaving” with telephone lines, connecting subscribers and ensuring that the network runs smoothly:
Upon the magic looms of the Bell System, tens of millions of telephone messages are daily woven into a marvelous fabric, representing the countless activities of a busy people. Day and night, invisible hands shift the shuttles to and fro, weaving the thoughts of men and women into a pattern which, if it could be seen as a tapestry, would tell a dramatic story of our business and social life.39
The weavers of speech are “out of sight of the subscribers…swiftly and skillfully interlacing the cords which guide the human voice over the country in all directions.” The telephone network “must be vitalized with the skill and intelligence which, in the Bell System, have made Universal Service the privilege of millions.” The accompanying image of an operator delicately handling telephone lines, connecting towns and neighbors, recalls the nimble fingers and soft voices of the early telephone operators, and the care with which this woman manages the network solidifies the idea that this medium labor is about, in the words of Alexander Graham Bell, “protecting” the network.
It would seem the quote tweet often weaves with this same care, connecting together the “filter bubbles” that are the source of so much hand-wringing. Who are the weavers of speech now, and what techniques do they use? How have those techniques been honed over centuries of rhetorical practice? These are the crucial questions that I have only begun to address here. The quote tweet is one example of how these connections are made. There are plenty of voices that reach outside of their so-called enclaves of agreement, and they often do so in order engage in coordinated efforts to abuse and harass. The targets of that harassment are then forced to develop techniques for dealing with this problem. A historical perspective on these epicritical efforts demonstrates that the infrastructure itself is unhealthy, not only due to negligent design by companies like Twitter but also because of a historically established set of commitments that push responsibility on to marginalized people, relying on them to make the connections, from weaving the tapestry of the Bell network to serving as the thin, precarious edges of our contemporary network graphs. When this epicritical labor is made public, we see who is ensuring that our digital spaces are usable and what techniques they are using to carry out that work.
Sarah T. Roberts, Behind the Screen: Content Moderation in the Shadows of Social Media (New Haven: Yale University Press, 2019), 37. ↩
Nick Statt, “YouTube Limits Moderators to Viewing Four Hours of Disturbing Content per Day,” The Verge, March 13, 2018, https://www.theverge.com/2018/3/13/17117554/youtube-content-moderators-limit-four-hours-sxsw. ↩
James J. Brown, Jr. and Hennis, Gregory, “Hateware and the Outsourcing of Responsibility,” in Digital Ethics: Rhetoric and Responsibility in Online Aggression, ed. Jessica Reyman and Erika M. Sparby (Routledge, 2019). ↩
This notion of “medium labor” is closely related to Rakow’s “gender work” which focuses on the close ties between gender and the telephone, though my aim is to take an intersectional approach to this set of problems as well. We rely on women, people of color, and LGBTQIA people for medium labor. See Lana Rakow, Gender on the Line: Women, the Telephone, and Community Life (University of Illinois Press, 1992). ↩
Richard A. Lanham, A Handlist of Rhetorical Terms (University of California Press Berkeley, 1991), 183. ↩
Lanham, A Handlist, 188. ↩
Wendy Hui Kyong Chun, Updating to Remain the Same: Habitual New Media (MIT Press, 2016), 85. ↩
Chun, Updating to Remain the Same, 86. ↩
Popular Electricity and the World’s Advance (Popular Electricity Publishing Company, 1912), 263. ↩
Popular Electricity and the World’s Advance, 264. ↩
Elizabeth Cobbs, The Hello Girls: America’s First Women Soldiers (Harvard University Press, 2017), 45. ↩
Kenneth Lipartito, “When Women Were Switches: Technology, Work, and Gender in the Telephone Industry, 1890-1920,” American Historical Review 99, no. 4 (1994): 1084. ↩
Alexander Graham Bell, “‘Early Telephony’ By Alexander Graham Bell. Address before the Telephone Society of Washington, Feb. 3 1910. Reproduced from Philadelphia Telephone News,” n.d., Box 399, Alexander Graham Bell Family Papers. ↩
Nan Johnson, Nineteenth-Century Rhetoric in North America (SIU Press, 1991), 74. ↩
Johnson, Nineteenth-Century Rhetoric, 73–74. ↩
Jacqueline Jones Royster, Traces of a Stream: Literacy and Social Change among African American Women (University of Pittsburgh Pre, 2000). ↩
Jessica Enoch, Refiguring Rhetorical Education: Women Teaching African American, Native American, and Chicano/a Students, 1865-1911 (SIU Press, 2008), 13. ↩
Venus Green, Race on the Line: Gender, Labor, and Technology in the Bell System, 1880–1980 (Duke University Press, 2001), 19. ↩
Green, Race on the Line, 18. ↩
Goggin, Maureen Daly, “An essamplaire essai on the rhetoricity of needlework sampler-making: A contribution to theorizing and historicizing rhetorical praxis,” Rhetoric Review 21, no. 4 (2002): 309-338. ↩
Melissa Villa-Nicholas, “The Invisible Information Worker: Latinas in Telecommunications,” in The Intersectional Internet: Race, Sex, Class, and Culture Online, ed. Safiya Umoja Noble and Brendesha M. Tynes (Peter Lang International Academic Publishers, 2016), 195. ↩
Kerry Segrave, The Women Who Got America Talking: Early Telephone Operators, 1878-1922 (Jefferson, North Carolina: McFarland & Company, 2017). ↩
Segrave, The Women Who Got America Talking, 111. ↩
Segrave, The Women Who Got America Talking, 116. ↩
Segrave, The Women Who Got America Talking. ↩
Segrave, The Women Who Got America Talking, 116. ↩
One anonymous reviewer of this essay relayed the following anecdote, which demonstrates that the expectations placed on the operator sometimes extended to the subscriber as well: “I grew up in a town with live telephone operators. They said ‘number please’ and if you gave the number without saying “please” in return there was an awkward pause while the waited for the “…please.” So that kind of protocol disciplining goes both ways.” ↩
Telephony: The American Telephone Journal … (Telephony Publishing Company, 1920), 30. ↩
Michael D. Smith and Norman N. Morra, “Obscene and Threatening Telephone Calls to Women: Data from a Canadian National Survey,” Gender & Society 8, no. 4 (1994): 584–596. ↩
“What to Do about Annoying Phone Calls,” n.d., ItemNumber: DOC-0088-000041, AT&T Corporate Archive. ↩
“Bell Information File 6A.3, Annoyance Calls, Line Identification,” n.d., DOC-0021-033479, AT&T Corporate Archive. ↩
Charlie Warzel, “Not Sure You Could Come up with a Feature Less Inclined toward Healthy Conversation than Quote RTing If You Tried.,” Tweet, @cwarzel (blog), June 17, 2018, https://twitter.com/cwarzel/status/1008570844124069889. ↩
Leo Graiden Stewart et al., “Drawing the Lines of Contention: Networked Frame Contests Within #BlackLivesMatter Discourse,” Proceedings of the ACM on Human-Computer Interaction 1, no. CSCW (December 6, 2017): 96, https://doi.org/10.1145/3134920. ↩
Stewart et al., “Drawing the Lines of Contention,” 15, emphasis added. ↩
Jeffrey Walker, Rhetoric and Poetics in Antiquity, 1 edition (Oxford ; New York: Oxford University Press, 2000). ↩
Sasha Costanza-Chock, “Design Justice: Towards an Intersectional Feminist Framework for Design Theory and Practice,” SSRN Scholarly Paper (Rochester, NY: Social Science Research Network, June 3, 2018), https://papers.ssrn.com/abstract=3189696. ↩
Safiya Umoja Noble, Algorithms of Oppression: How Search Engines Reinforce Racism (New York: NYU Press, 2018); Cathy O’Neil, Weapons of Math Destruction: How Big Data Increases Inequality and Threatens Democracy (New York: Crown, 2016). ↩
A 2017 Pew study found that 1 in four blacks reported being harassed due to their race and that women are about twice as likely as men to say they have been targeted as a result of their gender. See: Maeve Duggan, “Online Harassment,” Pew Research Center: Internet, Science & Tech (blog), October 22, 2014, http://www.pewinternet.org/2014/10/22/online-harassment/. ↩
“Weavers of Speech,” Bell Telephone News, December 1915. ↩
Article: Creative Commons Attribution 3.0 Unported License.
Image: "Intereactions," (Screenshots) by Eric Schmaltz with Kevin McPhee and Graeme Ring (2017).